フレッツ 光クロス + v6プラス固定IPをpfSenseで利用する
2023年12月20日より、「フレッツ 光クロス」サービスが北海道札幌市の一部で提供開始された。
フレッツ光クロスを収容するために、以下の小型PCを調達したところ、pfSenseがプリインストールされており、これを活用してみることにした。
光クロス用の小型PCが届いた🙆♂️
— pirosap (@pirosap) December 21, 2023
みんなR86Sを買っているTLではありますが、この子は1111セールで大変お得だったTOPTON
Intel RaptorLake U300E
Intel X520 82599ES 10G SFP+ x2
Intel I226-V 2.5GbE x 4
最初からpfSenseが入ってた
6万しないのにちゃんと動いてエグいなー pic.twitter.com/PPsh7y5mtI
光クロスで提供される10G-ONUは、10GBASE-Tのインターフェースであり、小型PCのSFP+に接続するためには10GBASE-T SFP+のモジュールが必要となる。しかし、10GBASE-T SFP+モジュールは大変熱を持つため、10G-ONUと小型PCの間にメディアコンバーターを設置し、10G SFP+ DACで接続することとした。
回線は、光コラボ事業者の enひかりにて、enひかりクロス+固定IP(v6プラス)オプションを契約している。
v6プラスによる固定IPオプションは、IPIPトンネルを張るだけなので構成が容易な利点がある。
以下、pfSenseの設定。バージョンは 2.7.2-RELEASE (amd64)。
WANとして10G-ONUに接続している ix0インターフェースを、LANとしてix1インターフェースをアサインする。
WANインターフェースの設定
IPv4 Configuration Type : None
IPv6 Configuration Type : DHCP6
DHCP6 Client Configuration / DHCPv6 Prefix Delegation size : 56
Send IPv6 prefix hint : ☑
Do not wait for a RA : ☑

LANインターフェースの設定
IPv4 Configuration Type : Static IPv4
IPv6 Configuration Type : Track Interface
Static IPv4 Configuration / IPv4 Address : 192.168.1.1 / 24 (※お好みで)
Track IPv6 Interface : WAN

ここまでの設定で、LANインターフェース側にv6アドレスが付与され、Status / Interfaces で確認できるので、IPv6プレフィックスを控えておく。
IPv6アドレスが上手く付与されない場合は、インターフェースを disable/enableしたりすると付与されることがあった。
JPIXで払い出される固定IP設定として、enひかりクロスでは以下の情報が通知された。
<v4IPアドレス> x.x.x.x/32
<IPv6プレフィックス> 開通時に決定
<インターフェイスID> xxxx:aaaa:bbbb:0000
<BRアドレス> 2404:9200:225:100::65
<ユーザID> myuserid
<パスワード> password
LANインターフェースで確認したIPv6プレフィックスと、インターフェースIDをつなげて、Firewall / Virtual IPsを作成する。
Type : IP Alias
Interface : WAN
Address type : Single address
Address(es) : IPv6プレフィックス:インターフェースID / 56

Interfaces / GIFs でGIFを作成する。
Parent Interface : Virtual IPで作成したアドレスを選択
GIF Remote Address : 通知されたBRアドレス
GIF tunnel local address : 割り当てられた固定IPv4アドレス
GIF tunnel remote address : 任意のIPアドレス(最終的に、tracerouteでのnext hopアドレスにした)
GIF tunnel subnet : 32

Interfaces / Interface Assignments
GIFをOPT1に割り当てて、MTU : 1460、MSS:1420にしておく。

System / Routing / Gateways
WAN_DHCP6 と OPT1_TUNNELV4それぞれで
Gateway Monitoring : ☑ Disable Gateway Monitoring


System / Routing / Gateways
Default gateway IPv4 : OPT1_TUNNELV4
Default gateway IPv6 : WAN_DHCP6

Firewall / NAT / Outbound
Manual Outbound NAT rule generation. (AON - Advanced Outbound NAT)
Auto created rule ~ で設定が入っている
shellから、以下を実行
curl "http://fcs.enabler.ne.jp/update?user=myuserid&pass=password"
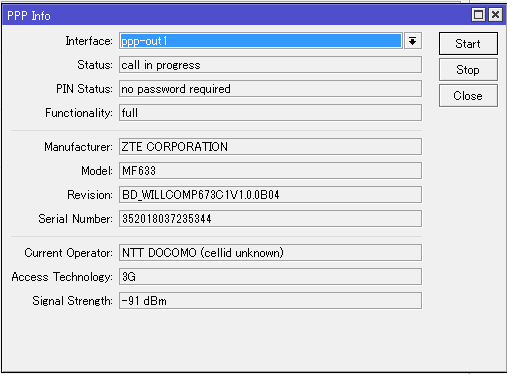
10Gで接続したクライアントにて、動作確認。

"Passpoint による Wi-Fi 環境の構築・運用ガイド" をC96で頒布しました
コミックマーケット96 4日目(2019/8/12)にて、初めての本となります "Passpoint によるWi-Fi環境の構築・運用ガイド" を頒布してきました。

暑い中、手に取っていただいた皆様、ありがとうございました。
持ち込んだのは40部でしたが、おかげさまで13時前には完売することができました。
事前にTwitterでは告知させていただいていたのですが、想像していたより多くの方が来ていただいてとてもうれしかったです。
ブースをお手伝いいただいた皆様、お隣のブースの 次世代無線LAN準備会様、glenda9様、ありがとうございました。
当日の様子を、お手伝いいただいていた@jyamagさんが流してくれていました。ありがとうございます。
コミケ無線LAN三銃士! pic.twitter.com/Q9Sc3QpKVh
— J_Yamaguchi (@jyamag) 2019年8月12日
コミケ 無線LAN関連3ブース、リアル書籍は完売です。( @n_kane さんのところの電子版は購入可能です!) pic.twitter.com/GD7cqL5Kw9
— J_Yamaguchi (@jyamag) 2019年8月12日
この本は、筆者らが2017年ごろから取り組んでいる「Hotspot 2.0(Passpoint)」によるWi-Fi 環境の構築と運⽤についてまとめたものです。
感想をつぶやいて頂いていただいた皆様、ありがとうございます。
C97では自サークルでは参加しませんが、第2版を委託で出せたらいいな、と思っています。
routerboardの無線LAN周りの設定は、かなりこれにお世話になっています。特にPasspoint周りは、英語サイトにも情報がほとんどないので。 https://t.co/iT3ENj4vdW
— Hideaki_nomap (@hgot07) 2019年8月23日
pirosapさんの「PasspointによるWi-Fi環境の構築と運用」読了。そのうちやる予定のHotspot2.0遊びではこれを若者に渡しておくとよしなにやってくれるのでは?!という良い本でした。 pic.twitter.com/mqHXyd47zm
— えぬかね📡C96ありがとうございました (@n_kane) 2019年8月15日
ご来訪いただいたのに完売でお渡しできなかった方や、遠方なので他の方法で頒布してほしい、というお声もいただきましたので、boothでPDFの電子版を頒布させていただいています。
よろしければご利用ください。
Why your iOS device with the AT&T SIM automatically join to an AT&T Wi-Fi Hotspot aka "attwifi - Passpoint" without any user settings.
AT&TのSIMを挿したiPhoneは、何故自動的にAT&TのPasspoint基地局にWi-Fi接続するのか
Let me jump to the conclusion.
The Carrier Bundles from AT&T includes a profile to connect AT&T Wi-Fi Hotspot (Passpoint).
I read some AT&T user's point in the forum like below;
How to Disable ATT Passpoint IPhone 8+ iOS 11.0.2
Yesterday I was at a HomeDepot and nothing was loading on my phone. It turned out I was on ATT-Passpoint WiFi. Not LTE. The phone won’t let me “forget” that ssid and when I toggle AutoJoin off it just switches back on.
I don’t care what security ATT passpoint uses I just don’t want to auto join any public WiFi system. Anyone know how to disable this?
https://forums.att.com/t5/Apple/How-to-Disable-ATT-Passpoint-IPhone-8-iOS-11-0-2/td-p/5287613
Forced to join attwifi since iOS 11!!!!!
According to AT&T's info here https://passpoint.attwifi.com/ an iPhone needs a Passpoint profile installed to automatically connect. However, my phone does not have any profile installed. I imagine that they updated the carrier settings to "force" configure the phone to work with Passpoint if WiFi Calling is enabled, perhaps to coincide with the iOS11 release.
https://forums.imore.com/ask-question/394777-forced-join-attwifi-since-ios-11-a.html
And yes, Here is the mecanism.
AT&T updated with thier "Carrie Bundles" with iOS11.
We can see what does it have.
The following link is the apple carrier bundle list:
https://itunes.apple.com/WebObjects/MZStore.woa/wa/com.apple.jingle.appserver.client.MZITunesClientCheck/version
It has the BundleURL list, iOS11.1 will see this URL.
<key>ATT_US</key> <dict> --- snip -- <key>11.1</key> <dict> <key>BuildVersion</key> <string>30.1</string> <key>BundleURL</key> <string>http://appldnld.apple.com/ios11.1/carrierbundles/091-43117-20171030-22774A0C-BD87-11E7-92F2-91FF17FB103A/ATT_US_iPhone.ipcc</string> <key>Digest</key> <data> +0Eoo93OM5FX2iXr6WiHNRQDHr0= </data> </dict> --- snip --- </dict>
The .ipcc file is ZIP archive.
Here is file list.
Dutch.lproj hi.lproj overrides_N56_N61.pri English.lproj hr.lproj overrides_N66_N71.der.pri French.lproj hu.lproj overrides_N66_N71.plist German.lproj id.lproj overrides_N69.plist Info.plist ko.lproj overrides_N69.pri Italian.lproj ms.lproj pl.lproj Japanese.lproj no.lproj profile.mobileconfig Spanish.lproj overrides_D101_D111.der.pri pt.lproj ar.lproj overrides_D101_D111.plist pt_PT.lproj ca.lproj overrides_D10_D11.der.pri ro.lproj carrier.plist overrides_D10_D11.plist ru.lproj cs.lproj overrides_D201_D211.der.pri signatures da.lproj overrides_D201_D211.plist sk.lproj el.lproj overrides_D20_D21.der.pri sv.lproj en_AU.lproj overrides_D20_D21.plist th.lproj en_GB.lproj overrides_D22.der.pri tr.lproj es_MX.lproj overrides_D22.plist uk.lproj fi.lproj overrides_D221.der.pri version.plist fr_CA.lproj overrides_D221.plist vi.lproj global_setting_A.gri overrides_N51_N53.plist zh_CN.lproj global_setting_B.gri overrides_N51_N53.pri zh_HK.lproj he.lproj overrides_N56_N61.plist zh_TW.lproj
The profile.mobileconfig include the settings to autojoin the network of AT&T Wi-Fi Passpoint with the EAP-SIM/AKA authentication.
It does not have SSID as attwifi-Passpoint because it is Passpoint.
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>PayloadContent</key> <array> <dict> <key>PayloadDescription</key> <string>Configures device restrictions.</string> <key>PayloadDisplayName</key> <string>Restrictions</string> <key>PayloadIdentifier</key> <string>com.apple.attwifi.restrictions</string> <key>PayloadOrganization</key> <string>Apple Inc</string> <key>PayloadType</key> <string>com.apple.applicationaccess</string> <key>PayloadUUID</key> <string>E1390FCE-911C-4B64-B352-8CE4B5E3A891</string> <key>PayloadVersion</key> <integer>1</integer> <key>allowAddingGameCenterFriends</key> <true/> <key>allowAppInstallation</key> <true/> <key>allowCamera</key> <true/> <key>allowExplicitContent</key> <true/> <key>allowGlobalBackgroundFetchWhenRoaming</key> <true/> <key>allowInAppPurchases</key> <true/> <key>allowMultiplayerGaming</key> <true/> <key>allowSafari</key> <true/> <key>allowScreenShot</key> <true/> <key>allowVideoConferencing</key> <true/> <key>allowVoiceDialing</key> <true/> <key>allowYouTube</key> <true/> <key>allowiTunes</key> <true/> <key>forceEncryptedBackup</key> <false/> <key>ratingApps</key> <integer>1000</integer> <key>ratingMovies</key> <integer>1000</integer> <key>ratingRegion</key> <string>us</string> <key>ratingTVShows</key> <integer>1000</integer> <key>safariAcceptCookies</key> <integer>2</integer> <key>safariAllowAutoFill</key> <true/> <key>safariAllowJavaScript</key> <true/> <key>safariAllowPopups</key> <true/> <key>safariForceFraudWarning</key> <false/> </dict> <dict> <key>EncryptionType</key> <string>None</string> <key>HIDDEN_NETWORK</key> <false/> <key>IsHotspot</key> <true/> <key>PayloadDescription</key> <string>Configures wireless connectivity settings.</string> <key>PayloadDisplayName</key> <string>Wi-Fi (attwifi)</string> <key>PayloadIdentifier</key> <string>com.apple.attwifi.wifi</string> <key>PayloadOrganization</key> <string>Apple Inc</string> <key>PayloadType</key> <string>com.apple.wifi.managed</string> <key>PayloadUUID</key> <string>9CB34BD4-FF73-4E49-8474-DA475B13E2C6</string> <key>PayloadVersion</key> <integer>1</integer> <key>SSID_STR</key> <string>attwifi</string> </dict> <dict> <key>AutoJoin</key> <true/> <key>DisplayedOperatorName</key> <string>AT&T Wi-Fi Passpoint</string> <key>DomainName</key> <string>attwifi.com</string> <key>EAPClientConfiguration</key> <dict> <key>AcceptEAPTypes</key> <array> <integer>23</integer> </array> <key>EAPSIMAKAConservativePeer</key> <true/> <key>EAPSIMAKAPsudeonymIdentityLifetimeHours</key> <integer>24</integer> </dict> <key>EncryptionType</key> <string>WPA2</string> <key>IsHotspot</key> <true/> <key>MCCAndMNCs</key> <array> <string>310410</string> </array> <key>PayloadDescription</key> <string>Configures Wi-Fi settings</string> <key>PayloadDisplayName</key> <string>WiFi</string> <key>PayloadIdentifier</key> <string>com.apple.attwifi.com.apple.wifi.managed.C7F682EC-9305-4E07-A1AB-BEB24B1E5611</string> <key>PayloadType</key> <string>com.apple.wifi.managed</string> <key>PayloadUUID</key> <string>865A5DF1-1AE7-4659-85D8-B686E29BB1AE</string> <key>PayloadVersion</key> <integer>1</integer> <key>ProxyType</key> <string>None</string> <key>ServiceProviderRoamingEnabled</key> <true/> </dict> </array> <key>PayloadDescription</key> <string>Auto-joins the attwifi Wi-Fi network</string> <key>PayloadDisplayName</key> <string>attwifi</string> <key>PayloadIdentifier</key> <string>com.apple.attwifi</string> <key>PayloadOrganization</key> <string>Apple Inc</string> <key>PayloadRemovalDisallowed</key> <false/> <key>PayloadType</key> <string>Configuration</string> <key>PayloadUUID</key> <string>7156353A-F9C3-42AE-A781-2DD301ACBBD0</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </plist>
(参考)AT&T Wi-Fi Passpoint (w/ EAP-AKA) のiOS用プロファイル
Portable Wi-Fi Hotspots & Mobile Wi-Fi Plans - AT&T
https://www.att.com/shop/wireless/wifi.html
At&T Wi-Fi Passpoint
https://passpoint.attwifi.com/
iOSでアクセスするとプロファイルが落とせるが、プロファイルのダウンロードに認証が求められないのでEAP-AKAかEAP-SIM認証のはず。
落としてApple Configurator 2で署名削除してみたらこんな感じだった。
EAPTypesが23なので、EAP-AKA。
MCC(310)とMNC(410)が埋め込まれてる。
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>ConsentText</key> <dict> <key>default</key> <string>You understand that installation of this profile will configure your device to automatically connect at Wi-Fi Passpoint-enabled hot spots where AT&T Mobility subscribers are authorized. You agree that you will not install this profile (i) if you are not running Apple iOS 9.0 or later, or (ii) if you are not an AT&T Mobility subscriber. If you choose to install the profile on other devices, you do so at your own risk. All connections are subject to the Terms of Service that apply at that hot spot, including the AT&T Wi-Fi Terms of Service available at http://www.att.com/legal/terms.wiFiServices.html. If you wish to discontinue automatic connection at Passpoint-enabled hot spots, please delete the profile from your Wi-Fi settings. </string> </dict> <key>PayloadContent</key> <array> <dict> <key>AutoJoin</key> <true/> <key>DisplayedOperatorName</key> <string>AT&T Wi-Fi Passpoint</string> <key>DomainName</key> <string>attwifi.com</string> <key>EAPClientConfiguration</key> <dict> <key>AcceptEAPTypes</key> <array> <integer>23</integer> </array> </dict> <key>EncryptionType</key> <string>WPA2</string> <key>HIDDEN_NETWORK</key> <false/> <key>IsHotspot</key> <true/> <key>MCCAndMNCs</key> <array> <string>310410</string> </array> <key>PayloadDescription</key> <string>Configures Wi-Fi settings</string> <key>PayloadDisplayName</key> <string>Wi-Fi</string> <key>PayloadIdentifier</key> <string>com.apple.wifi.managed.4A766A24-2257-4132-A68C-37FFEB2054E5</string> <key>PayloadType</key> <string>com.apple.wifi.managed</string> <key>PayloadUUID</key> <string>4A766A24-2257-4132-A68C-37FFEB2054E5</string> <key>PayloadVersion</key> <real>1</real> <key>ProxyType</key> <string>None</string> <key>ServiceProviderRoamingEnabled</key> <true/> </dict> </array> <key>PayloadDescription</key> <string>This profile enables highly-secure, automatic connections for AT&T Mobility subscribers at participating public hot spots.</string> <key>PayloadDisplayName</key> <string>AT&T Wi-Fi Passpoint</string> <key>PayloadIdentifier</key> <string>com.attwifi.passpoint</string> <key>PayloadOrganization</key> <string>AT&T</string> <key>PayloadRemovalDisallowed</key> <false/> <key>PayloadType</key> <string>Configuration</string> <key>PayloadUUID</key> <string>325CDD32-3E59-40A1-9E78-F4A95044E813</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </plist>
なるほど。
MikroTik hAP acで作るHotspot 2.0環境 (プロファイルをインストールできて繋がった端末のログ)
MikroTik hAP acで作るHotspot 2.0環境 (Android編) - pirosapの備忘録
MikroTik hAP acで作るHotspot 2.0環境 (プロファイルをインストールできない端末のログを見てみる) - pirosapの備忘録
の続き。
前回作ったAndroid用のプロファイルがインストールできてHotspot 2.0につながる端末のログ。
実機を開発者向けオプションから、USBデバッグを有効にして、PCとUSBで接続する。
Android One S1 (Android 7.0 / Build 00WW_1_15I)
Android One S1 をご利用中のお客さまへ ~最新ソフトウェア配信のお知らせ~ | ワイモバイル(Y!mobile) のバージョン。
古いファームでどうだったかの記録用。
aruba-HS20に最終的に接続できているが、このファームではオペレータ名が実機のWi-Fi設定画面などには表示されなかった。
05-12 22:03:01.913 I/ActivityManager( 2310): START u0 {act=android.intent.action.VIEW dat=content://downloads/all_downloads/18 typ=application/x-wifi-config flg=0x10000001 cmp=com.android.certinstaller/.CertInstallerMain} from uid 10063 on display 0
05-12 22:03:01.923 E/ANDR-PERF-MPCTL( 1792): Invalid profile no. 0, total profiles 0 only
05-12 22:03:01.932 D/ActivityTrigger( 2310): ActivityTrigger activityPauseTrigger
05-12 22:03:01.949 E/ConnectivityManager.CallbackHandler( 7777): callback not found for RELEASED message
05-12 22:03:01.963 I/ActivityManager( 2310): Start proc 8060:com.android.certinstaller/u0a42 for activity com.android.certinstaller/.CertInstallerMain
05-12 22:03:01.963 V/BoostFramework( 2310): BoostFramework() : mPerf = com.qualcomm.qti.Performance@d615a1f
05-12 22:03:02.007 W/System ( 8060): ClassLoader referenced unknown path: /system/app/CertInstaller/lib/arm64
05-12 22:03:02.063 I/ActivityManager( 2310): START u0 {cmp=com.android.certinstaller/.WiFiInstaller (has extras)} from uid 10042 on display 0
05-12 22:03:02.066 D/ActivityTrigger( 2310): ActivityTrigger activityPauseTrigger
05-12 22:03:02.079 I/HAL ( 8060): loaded HAL id=gralloc path=/system/lib64/hw/gralloc.msm8937.so hmi=0x7fd6c16d10 handle=0xe16bd971b5171207
05-12 22:03:02.105 I/Adreno ( 8060): QUALCOMM build : 15ca084, I4f723aa5a2
05-12 22:03:02.105 I/Adreno ( 8060): Build Date : 11/28/16
05-12 22:03:02.105 I/Adreno ( 8060): OpenGL ES Shader Compiler Version: XE031.09.00.03
05-12 22:03:02.105 I/Adreno ( 8060): Local Branch :
05-12 22:03:02.105 I/Adreno ( 8060): Remote Branch : refs/tags/AU_LINUX_ANDROID_LA.UM.5.5.R1.07.00.00.269.016
05-12 22:03:02.105 I/Adreno ( 8060): Remote Branch : NONE
05-12 22:03:02.105 I/Adreno ( 8060): Reconstruct Branch : NOTHING
05-12 22:03:02.107 D/WifiInstaller( 8060): WiFi data for wifi-config: application/x-wifi-config is 7141
05-12 22:03:02.109 D/WCFG ( 2310): Content: 7141
05-12 22:03:02.109 D/WCFG ( 2310): Decoded: 5286 bytes.
05-12 22:03:02.111 I/OpenGLRenderer( 8060): Initialized EGL, version 1.4
05-12 22:03:02.111 D/OpenGLRenderer( 8060): Swap behavior 1
05-12 22:03:02.130 V/DownloadManager( 3596): Deleting /storage/emulated/0/Download/pirosap-tech-20170429.config via provider delete
05-12 22:03:02.132 D/MediaProvider( 3596): object removed 45
05-12 22:03:02.157 D/HS20 ( 2310): plain MIME container, boundary '{boundary}', type 'application/x-passpoint-profile', encoding [base64]
05-12 22:03:02.158 D/HS20 ( 2310): plain MIME container, boundary '{boundary}', type 'application/x-x509-ca-cert', encoding [base64]
05-12 22:03:02.159 D/HS20 ( 2310): multipart MIME container, boundary 'null', type 'multipart/mixed', encoding [base64]
05-12 22:03:02.159 D/WCFG ( 2310): + Content Type: application/x-passpoint-profile
05-12 22:03:02.160 D/WCFG ( 2310): OMA: <MgmtTree xmlns="syncml:dmddf1.2">
05-12 22:03:02.160 D/WCFG ( 2310): <VerDTD>1.2</VerDTD>
05-12 22:03:02.160 D/WCFG ( 2310): <Node>
05-12 22:03:02.160 D/WCFG ( 2310): <NodeName>PerProviderSubscription</NodeName>
05-12 22:03:02.160 D/WCFG ( 2310): <RTProperties>
05-12 22:03:02.160 D/WCFG ( 2310): <Type>
05-12 22:03:02.160 D/WCFG ( 2310): <DDFName>urn:wfa:mo:hotspot2dot0-perprovidersubscription:1.0</DDFName>
05-12 22:03:02.160 D/WCFG ( 2310): </Type>
05-12 22:03:02.160 D/WCFG ( 2310): </RTProperties>
05-12 22:03:02.160 D/WCFG ( 2310): <Node>
05-12 22:03:02.160 D/WCFG ( 2310): <NodeName>X1</NodeName>
05-12 22:03:02.160 D/WCFG ( 2310): <Node>
05-12 22:03:02.160 D/WCFG ( 2310): <NodeName>Credential</NodeName>
05-12 22:03:02.160 D/WCFG ( 2310): <Node>
05-12 22:03:02.160 D/WCFG ( 2310): <NodeName>CreationDate</NodeName>
05-12 22:03:02.160 D/WCFG ( 2310): <Value>2017-02-16T14:21:36Z</Value>
05-12 22:03:02.160 D/WCFG ( 2310): </Node>
05-12 22:03:02.160 D/WCFG ( 2310): <Node>
05-12 22:03:02.160 D/WCFG ( 2310): <NodeName>UsernamePassword</NodeName>
05-12 22:03:02.160 D/WCFG ( 2310): <Node>
05-12 22:03:02.160 D/WCFG ( 2310): <NodeName>MachineManaged</NodeName>
05-12 22:03:02.160 D/WCFG ( 2310): <Value>true</Value>
05-12 22:03:02.160 D/WCFG ( 2310): </Node>
05-12 22:03:02.160 D/WCFG ( 2310): <Node>
05-12 22:03:02.160 D/WCFG ( 2310): <NodeName>EAPMethod</NodeName>
05-12 22:03:02.160 D/WCFG ( 2310): <Node>
05-12 22:03:02.160 D/WCFG ( 2310): <NodeName>EAPType</NodeName>
05-12 22:03:02.160 D/WCFG ( 2310): <Value>21</Value>
05-12 22:03:02.160 D/WCFG ( 2310): </Node>
05-12 22:03:02.160 D/WCFG ( 2310): <Node>
05-12 22:03:02.160 D/WCFG ( 2310): <NodeName>InnerMethod</NodeName>
05-12 22:03:02.160 D/WCFG ( 2310): <Value>MS-CHAP-V2</Value>
05-12 22:03:02.160 D/WCFG ( 2310): </Node>
05-12 22:03:02.160 D/WCFG ( 2310): </Node>
05-12 22:03:02.160 D/WCFG ( 2310): <Node>
05-12 22:03:02.160 D/WCFG ( 2310): <NodeName>Username</NodeName>
05-12 22:03:02.160 D/WCFG ( 2310): <Value>hoge</Value>
05-12 22:03:02.160 D/WCFG ( 2310): </Node>
05-12 22:03:02.160 D/WCFG ( 2310): <Node>
05-12 22:03:02.160 D/WCFG ( 2310): <NodeName>Password</NodeName>
05-12 22:03:02.160 D/WCFG ( 2310): <Value>aHMyMCF0ZXN0MTc=</Value>
05-12 22:03:02.160 D/WCFG ( 2310): </Node>
05-12 22:03:02.160 D/WCFG ( 2310): </Node>
05-12 22:03:02.160 D/WCFG ( 2310): <Node>
05-12 22:03:02.160 D/WCFG ( 2310): <NodeName>Realm</NodeName>
05-12 22:03:02.160 D/WCFG ( 2310): <Value>pirosap.tech</Value>
05-12 22:03:02.160 D/WCFG ( 2310): </Node>
05-12 22:03:02.160 D/WCFG ( 2310): </Node>
05-12 22:03:02.160 D/WCFG ( 2310): <Node>
05-12 22:03:02.160 D/WCFG ( 2310): <NodeName>HomeSP</NodeName>
05-12 22:03:02.160 D/WCFG ( 2310): <Node>
05-12 22:03:02.160 D/WCFG ( 2310): <NodeName>FriendlyName</NodeName>
05-12 22:03:02.160 D/WCFG ( 2310): <Value>NGH testbed by pirosap.tech</Value>
05-12 22:03:02.160 D/WCFG ( 2310): </Node>
05-12 22:03:02.160 D/WCFG ( 2310): <Node>
05-12 22:03:02.160 D/WCFG ( 2310): <NodeName>FQDN</NodeName>
05-12 22:03:02.160 D/WCFG ( 2310): <Value>ngh.pirosap.tech</Value>
05-12 22:03:02.160 D/WCFG ( 2310): </Node>
05-12 22:03:02.160 D/WCFG ( 2310): </Node>
05-12 22:03:02.160 D/WCFG ( 2310): </Node>
05-12 22:03:02.160 D/WCFG ( 2310): </Node>
05-12 22:03:02.160 D/WCFG ( 2310): </MgmtTree>
05-12 22:03:02.160 D/WCFG ( 2310): + Content Type: application/x-x509-ca-cert
05-12 22:03:02.161 D/WCFG ( 2310): Cert subject CN=DST Root CA X3, O=Digital Signature Trust Co.
05-12 22:03:02.167 D/WCFG ( 2310): Full Cert: Certificate:
05-12 22:03:02.167 D/WCFG ( 2310): Data:
05-12 22:03:02.167 D/WCFG ( 2310): Version: 3 (0x2)
05-12 22:03:02.167 D/WCFG ( 2310): Serial Number:
05-12 22:03:02.167 D/WCFG ( 2310): 44:af:b0:80:d6:a3:27:ba:89:30:39:86:2e:f8:40:6b
05-12 22:03:02.167 D/WCFG ( 2310): Signature Algorithm: sha1WithRSAEncryption
05-12 22:03:02.167 D/WCFG ( 2310): Issuer: O=Digital Signature Trust Co., CN=DST Root CA X3
05-12 22:03:02.167 D/WCFG ( 2310): Validity
05-12 22:03:02.167 D/WCFG ( 2310): Not Before: Sep 30 21:12:19 2000 GMT
05-12 22:03:02.167 D/WCFG ( 2310): Not After : Sep 30 14:01:15 2021 GMT
05-12 22:03:02.167 D/WCFG ( 2310): Subject: O=Digital Signature Trust Co., CN=DST Root CA X3
05-12 22:03:02.167 D/WCFG ( 2310): Subject Public Key Info:
05-12 22:03:02.167 D/WCFG ( 2310): Public Key Algorithm: rsaEncryption
05-12 22:03:02.167 D/WCFG ( 2310): Public-Key: (2048 bit)
05-12 22:03:02.167 D/WCFG ( 2310): Modulus:
05-12 22:03:02.167 D/WCFG ( 2310): 00:df:af:e9:97:50:08:83:57:b4:cc:62:65:f6:90:
05-12 22:03:02.167 D/WCFG ( 2310): 82:ec:c7:d3:2c:6b:30:ca:5b:ec:d9:c3:7d:c7:40:
05-12 22:03:02.167 D/WCFG ( 2310): c1:18:14:8b:e0:e8:33:76:49:2a:e3:3f:21:49:93:
05-12 22:03:02.167 D/WCFG ( 2310): ac:4e:0e:af:3e:48:cb:65:ee:fc:d3:21:0f:65:d2:
05-12 22:03:02.167 D/WCFG ( 2310): 2a:d9:32:8f:8c:e5:f7:77:b0:12:7b:b5:95:c0:89:
05-12 22:03:02.167 D/WCFG ( 2310): a3:a9:ba:ed:73:2e:7a:0c:06:32:83:a2:7e:8a:14:
05-12 22:03:02.167 D/WCFG ( 2310): 30:cd:11:a0:e1:2a:38:b9:79:0a:31:fd:50:bd:80:
05-12 22:03:02.167 D/WCFG ( 2310): 65:df:b7:51:63:83:c8:e2:88:61:ea:4b:61:81:ec:
05-12 22:03:02.167 D/WCFG ( 2310): 52:6b:b9:a2:e2:4b:1a:28:9f:48:a3:9e:0c:da:09:
05-12 22:03:02.167 D/WCFG ( 2310): 8e:3e:17:2e:1e:dd:20:df:5b:c6:2a:8a:ab:2e:bd:
05-12 22:03:02.167 D/WCFG ( 2310): 70:ad:c5:0b:1a:25:90:74:72:c5:7b:6a:ab:34:d6:
05-12 22:03:02.167 D/WCFG ( 2310): 30:89:ff:e5:68:13:7b:54:0b:c8:d6:ae:ec:5a:9c:
05-12 22:03:02.167 D/WCFG ( 2310): 92:1e:3d:64:b3:8c:c6:df:bf:c9:41:70:ec:16:72:
05-12 22:03:02.167 D/WCFG ( 2310): d5:26:ec:38:55:39:43:d0:fc:fd:18:5c:40:f1:97:
05-12 22:03:02.167 D/WCFG ( 2310): eb:d5:9a:9b:8d:1d:ba:da:25:b9:c6:d8:df:c1:15:
05-12 22:03:02.167 D/WCFG ( 2310): 02:3a:ab:da:6e:f1:3e:2e:f5:5c:08:9c:3c:d6:83:
05-12 22:03:02.167 D/WCFG ( 2310): 69:e4:10:9b:19:2a:b6:29:57:e3:e5:3d:9b:9f:f0:
05-12 22:03:02.167 D/WCFG ( 2310): 02:5d
05-12 22:03:02.167 D/WCFG ( 2310): Exponent: 65537 (0x10001)
05-12 22:03:02.167 D/WCFG ( 2310): X509v3 extensions:
05-12 22:03:02.167 D/WCFG ( 2310): X509v3 Basic Constraints: critical
05-12 22:03:02.167 D/WCFG ( 2310): CA:TRUE
05-12 22:03:02.167 D/WCFG ( 2310): X509v3 Key Usage: critical
05-12 22:03:02.167 D/WCFG ( 2310): Certificate Sign, CRL Sign
05-12 22:03:02.167 D/WCFG ( 2310): X509v3 Subject Key Identifier:
05-12 22:03:02.167 D/WCFG ( 2310): C4:A7:B1:A4:7B:2C:71:FA:DB:E1:4B:90:75:FF:C4:15:60:85:89:10
05-12 22:03:02.167 D/WCFG ( 2310): Signature Algorithm: sha1WithRSAEncryption
05-12 22:03:02.167 D/WCFG ( 2310): a3:1a:2c:9b:17:00:5c:a9:1e:ee:28:66:37:3a:bf:83:c7:3f:
05-12 22:03:02.167 D/WCFG ( 2310): 4b:c3:09:a0:95:20:5d:e3:d9:59:44:d2:3e:0d:3e:bd:8a:4b:
05-12 22:03:02.167 D/WCFG ( 2310): a0:74:1f:ce:10:82:9c:74:1a:1d:7e:98:1a:dd:cb:13:4b:b3:
05-12 22:03:02.167 D/WCFG ( 2310): 20:44:e4:91:e9:cc:fc:7d:a5:db:6a:e5:fe:e6:fd:e0:4e:dd:
05-12 22:03:02.167 D/WCFG ( 2310): b7:00:3a:b5:70:49:af:f2:e5:eb:02:f1:d1:02:8b:19:cb:94:
05-12 22:03:02.167 D/WCFG ( 2310): 3a:5e:48:c4:18:1e:58:19:5f:1e:02:5a:f0:0c:f1:b1:ad:a9:
05-12 22:03:02.167 D/WCFG ( 2310): dc:59:86:8b:6e:e9:91:f5:86:ca:fa:b9:66:33:aa:59:5b:ce:
05-12 22:03:02.167 D/WCFG ( 2310): e2:a7:16:73:47:cb:2b:cc:99:b0:37:48:cf:e3:56:4b:f5:cf:
05-12 22:03:02.167 D/WCFG ( 2310): 0f:0c:72:32:87:c6:f0:44:bb:53:72:6d:43:f5:26:48:9a:52:
05-12 22:03:02.167 D/WCFG ( 2310): 67:b7:58:ab:fe:67:76:71:78:db:0d:a2:56:14:13:39:24:31:
05-12 22:03:02.167 D/WCFG ( 2310): 85:a2:a8:02:5a:30:47:e1:dd:50:07:bc:02:09:90:00:eb:64:
05-12 22:03:02.167 D/WCFG ( 2310): 63:60:9b:16:bc:88:c9:12:e6:d2:7d:91:8b:f9:3d:32:8d:65:
05-12 22:03:02.167 D/WCFG ( 2310): b4:e9:7c:b1:57:76:ea:c5:b6:28:39:bf:15:65:1c:c8:f6:77:
05-12 22:03:02.167 D/WCFG ( 2310): 96:6a:0a:8d:77:0b:d8:91:0b:04:8e:07:db:29:b6:0a:ee:9d:
05-12 22:03:02.167 D/WCFG ( 2310): 82:35:35:10
05-12 22:03:02.200 V/BoostFramework( 8060): mAcquireFunc method = public int com.qualcomm.qti.Performance.perfLockAcquire(int,int[])
05-12 22:03:02.200 V/BoostFramework( 8060): mReleaseFunc method = public int com.qualcomm.qti.Performance.perfLockRelease()
05-12 22:03:02.200 V/BoostFramework( 8060): mAcquireTouchFunc method = public int com.qualcomm.qti.Performance.perfLockAcquireTouch(android.view.MotionEvent,android.util.DisplayMetrics,int,int[])
05-12 22:03:02.200 V/BoostFramework( 8060): mIOPStart method = public int com.qualcomm.qti.Performance.perfIOPrefetchStart(int,java.lang.String)
05-12 22:03:02.200 V/BoostFramework( 8060): mIOPStop method = public int com.qualcomm.qti.Performance.perfIOPrefetchStop()
05-12 22:03:02.216 V/BoostFramework( 8060): BoostFramework() : mPerf = com.qualcomm.qti.Performance@34306de
05-12 22:03:02.216 V/BoostFramework( 8060): BoostFramework() : mPerf = com.qualcomm.qti.Performance@d55c0bf
05-12 22:03:02.227 V/BoostFramework( 8060): BoostFramework() : mPerf = com.qualcomm.qti.Performance@904b542
05-12 22:03:02.227 V/BoostFramework( 8060): BoostFramework() : mPerf = com.qualcomm.qti.Performance@9477953
05-12 22:03:02.229 V/BoostFramework( 8060): BoostFramework() : mPerf = com.qualcomm.qti.Performance@12ce38e
05-12 22:03:02.229 V/BoostFramework( 8060): BoostFramework() : mPerf = com.qualcomm.qti.Performance@b4657af
05-12 22:03:02.303 I/iu.UploadsManager( 3390): End new media; added: 1, uploading: 0, time: 143 ms
05-12 22:03:02.339 I/ActivityManager( 2310): Displayed com.android.certinstaller/.WiFiInstaller: +253ms (total +390ms)
05-12 22:03:02.779 I/MSM-irqbalance( 1927): Decided to move IRQ3 from CPU1 [P:0] to CPU5 [P:1] (banned)
05-12 22:03:02.779 I/MSM-irqbalance( 1927): Decided to move IRQ3 from CPU0 [P:0] to CPU6 [P:1] (banned)
05-12 22:03:02.780 I/MSM-irqbalance( 1927): Decided to move IRQ5 from CPU0 [P:0] to CPU4 [P:1] (banned)
05-12 22:03:02.780 I/MSM-irqbalance( 1927): Decided to move IRQ3 from CPU3 [P:0] to CPU7 [P:1] (banned)
05-12 22:03:02.780 I/MSM-irqbalance( 1927): Decided to move IRQ5 from CPU3 [P:0] to CPU5 [P:1] (banned)
05-12 22:03:02.780 I/MSM-irqbalance( 1927): Decided to move IRQ3 from CPU2 [P:0] to CPU6 [P:1] (banned)
05-12 22:03:02.780 I/MSM-irqbalance( 1927): Decided to move IRQ5 from CPU2 [P:0] to CPU4 [P:1] (banned)
05-12 22:03:03.220 I/WindowManager( 2310): Destroying surface Surface(name=Toast) called by com.android.server.wm.WindowStateAnimator.destroySurface:2014 com.android.server.wm.WindowStateAnimator.destroySurfaceLocked:881 com.android.server.wm.WindowState.destroyOrSaveSurface:2073 com.android.server.wm.WindowSurfacePlacer.performSurfacePlacementInner:429 com.android.server.wm.WindowSurfacePlacer.performSurfacePlacementLoop:232 com.android.server.wm.WindowSurfacePlacer.performSurfacePlacement:180 com.android.server.wm.WindowManagerService$H.handleMessage:8110 android.os.Handler.dispatchMessage:102
05-12 22:03:05.489 I/ActivityManager( 2310): Process com.android.chrome:sandboxed_process0 (pid 7803) has died
05-12 22:03:05.490 D/ActivityManager( 2310): cleanUpApplicationRecord -- 7803
05-12 22:03:05.492 E/KernelCpuSpeedReader( 2310): Failed to read cpu-freq: /sys/devices/system/cpu/cpu0/cpufreq/stats/time_in_state (No such file or directory)
05-12 22:03:07.871 I/MSM-irqbalance( 1927): Decided to move IRQ3 from CPU2 [P:0] to CPU7 [P:1] (banned)
05-12 22:03:07.871 I/MSM-irqbalance( 1927): Decided to move IRQ5 from CPU2 [P:0] to CPU5 [P:1] (banned)
05-12 22:03:07.872 I/MSM-irqbalance( 1927): Decided to move IRQ3 from CPU3 [P:0] to CPU6 [P:1] (banned)
05-12 22:03:07.872 I/MSM-irqbalance( 1927): Decided to move IRQ5 from CPU3 [P:0] to CPU4 [P:1] (banned)
05-12 22:03:08.734 I/WindowManager( 2310): Destroying surface Surface(name=com.android.certinstaller/com.android.certinstaller.WiFiInstaller) called by com.android.server.wm.WindowStateAnimator.destroySurface:2014 com.android.server.wm.WindowStateAnimator.destroySurfaceLocked:881 com.android.server.wm.WindowState.destroyOrSaveSurface:2073 com.android.server.wm.AppWindowToken.destroySurfaces:363 com.android.server.wm.WindowStateAnimator.finishExit:565 com.android.server.wm.WindowStateAnimator.stepAnimationLocked:491 com.android.server.wm.WindowAnimator.updateWindowsLocked:303 com.android.server.wm.WindowAnimator.animateLocked:704
05-12 22:03:09.104 I/addOrUpdateNetwork( 2310): uid = 10042 SSID null nid=-1
05-12 22:03:09.107 I/WifiConfigStore( 2310): addOrUpdateNetwork created netId=0
05-12 22:03:09.108 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:09.110 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:09.111 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:09.113 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:09.117 D/WifiConfigStore( 2310): putting certificate CACERT_2044411083_WPA_EAPIEEE8021X_TTLS_MSCHAPV2 in keystore
05-12 22:03:09.120 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:09.121 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:09.122 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:09.123 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:09.124 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:09.125 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:09.126 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:09.127 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:09.128 D/WifiConfigManager( 2310): created new config netId=0 uid=10042 name=com.android.certinstaller
05-12 22:03:09.129 D/WifiConfigManager( 2310): created a homeSP object for 0:2044411083
05-12 22:03:09.134 E/WifiConfigStore( 2310): Failed to look-up a string: WAPI
05-12 22:03:09.134 E/WifiConfigStore( 2310): Failed to look-up a string: SMS4
05-12 22:03:09.135 E/WifiConfigStore( 2310): Failed to look-up a string: SMS4
05-12 22:03:09.142 D/HS20 ( 2310): Adding or updating HS20 profile for ngh.pirosap.tech
05-12 22:03:09.169 D/WifiNetworkHistory( 2310): saving network history: ngh.pirosap.techWPA_EAP gw: null Network Selection-status: NETWORK_SELECTION_ENABLED ephemeral=false choice:null link:0 status:0 nid:0 hasEverConnected: false
05-12 22:03:09.169 V/WifiNetworkHistory( 2310): writeKnownNetworkHistory write config ngh.pirosap.techWPA_EAP
05-12 22:03:09.181 I/ActivityManager( 2310): START u0 {cmp=com.android.certinstaller/.CredentialsInstallDialog (has extras)} from uid 10042 on display 0
05-12 22:03:09.193 D/ActivityTrigger( 2310): ActivityTrigger activityPauseTrigger
05-12 22:03:09.251 V/BoostFramework( 8060): BoostFramework() : mPerf = com.qualcomm.qti.Performance@40156d8
05-12 22:03:09.251 V/BoostFramework( 8060): BoostFramework() : mPerf = com.qualcomm.qti.Performance@17fa31
05-12 22:03:09.262 V/BoostFramework( 8060): BoostFramework() : mPerf = com.qualcomm.qti.Performance@e72be69
05-12 22:03:09.262 V/BoostFramework( 8060): BoostFramework() : mPerf = com.qualcomm.qti.Performance@b1540ee
05-12 22:03:09.265 V/BoostFramework( 8060): BoostFramework() : mPerf = com.qualcomm.qti.Performance@b3ee41c
05-12 22:03:09.265 V/BoostFramework( 8060): BoostFramework() : mPerf = com.qualcomm.qti.Performance@cefd825
05-12 22:03:09.407 I/ActivityManager( 2310): Displayed com.android.certinstaller/.CredentialsInstallDialog: +200ms
05-12 22:03:09.805 I/WindowManager( 2310): Destroying surface Surface(name=com.android.certinstaller/com.android.certinstaller.WiFiInstaller) called by com.android.server.wm.WindowStateAnimator.destroySurface:2014 com.android.server.wm.WindowStateAnimator.destroySurfaceLocked:881 com.android.server.wm.WindowState.removeLocked:1449 com.android.server.wm.WindowManagerService.removeWindowInnerLocked:2483 com.android.server.wm.WindowManagerService.removeWindowLocked:2441 com.android.server.wm.WindowManagerService.removeWindowLocked:2310 com.android.server.wm.WindowManagerService.removeWindow:2305 com.android.server.wm.Session.remove:193
05-12 22:03:11.827 D/ActivityTrigger( 2310): ActivityTrigger activityPauseTrigger
05-12 22:03:11.884 I/WindowManager( 2310): Destroying surface Surface(name=com.android.certinstaller/com.android.certinstaller.CredentialsInstallDialog) called by com.android.server.wm.WindowStateAnimator.destroySurface:2014 com.android.server.wm.WindowStateAnimator.destroySurfaceLocked:881 com.android.server.wm.WindowState.removeLocked:1449 com.android.server.wm.WindowManagerService.removeWindowInnerLocked:2483 com.android.server.wm.WindowManagerService.removeWindowLocked:2441 com.android.server.wm.WindowManagerService.removeWindowLocked:2310 com.android.server.wm.WindowManagerService.removeWindow:2305 com.android.server.wm.Session.remove:193
05-12 22:03:11.910 D/ActivityTrigger( 2310): ActivityTrigger activityPauseTrigger
05-12 22:03:11.917 W/InputMethodManagerService( 2310): Focus gain on non-focused client com.android.internal.view.IInputMethodClient$Stub$Proxy@a182bac (uid=10042 pid=8060)
05-12 22:03:11.925 I/WindowManager( 2310): Failed to capture screenshot of Token{d8e1140 ActivityRecord{69a34c3 u0 com.android.certinstaller/.CertInstallerMain t25 f}} appWin=Window{1ee6e17 u0 com.android.certinstaller/com.android.certinstaller.CertInstallerMain} drawState=4
05-12 22:03:11.928 E/ANDR-PERF-MPCTL( 1792): Invalid profile no. 0, total profiles 0 only
05-12 22:03:11.983 I/WindowManager( 2310): Destroying surface Surface(name=com.android.certinstaller/com.android.certinstaller.CertInstallerMain) called by com.android.server.wm.WindowStateAnimator.destroySurface:2014 com.android.server.wm.WindowStateAnimator.destroySurfaceLocked:881 com.android.server.wm.WindowState.removeLocked:1449 com.android.server.wm.WindowManagerService.removeWindowInnerLocked:2483 com.android.server.wm.WindowManagerService.removeWindowLocked:2441 com.android.server.wm.WindowManagerService.removeWindowLocked:2310 com.android.server.wm.WindowManagerService.removeWindow:2305 com.android.server.wm.Session.remove:193
05-12 22:03:12.009 I/WindowManager( 2310): Destroying surface Surface(name=com.android.certinstaller/com.android.certinstaller.CredentialsInstallDialog) called by com.android.server.wm.WindowStateAnimator.destroySurface:2014 com.android.server.wm.WindowStateAnimator.destroySurfaceLocked:881 com.android.server.wm.WindowState.destroyOrSaveSurface:2073 com.android.server.wm.AppWindowToken.destroySurfaces:363 com.android.server.wm.WindowStateAnimator.finishExit:565 com.android.server.wm.WindowStateAnimator.stepAnimationLocked:491 com.android.server.wm.WindowAnimator.updateWindowsLocked:303 com.android.server.wm.WindowAnimator.animateLocked:704
05-12 22:03:12.019 I/ActivityManager( 2310): Killing 7253:com.android.externalstorage/u0a10 (adj 906): empty #17
05-12 22:03:12.038 D/ActivityManager( 2310): cleanUpApplicationRecord -- 7253
05-12 22:03:12.237 I/iu.UploadsManager( 3390): End new media; added: 0, uploading: 0, time: 80 ms
05-12 22:03:12.548 I/WindowManager( 2310): Destroying surface Surface(name=Toast) called by com.android.server.wm.WindowStateAnimator.destroySurface:2014 com.android.server.wm.WindowStateAnimator.destroySurfaceLocked:881 com.android.server.wm.WindowState.destroyOrSaveSurface:2073 com.android.server.wm.WindowSurfacePlacer.performSurfacePlacementInner:429 com.android.server.wm.WindowSurfacePlacer.performSurfacePlacementLoop:232 com.android.server.wm.WindowSurfacePlacer.performSurfacePlacement:180 com.android.server.wm.WindowManagerService$H.handleMessage:8110 android.os.Handler.dispatchMessage:102
05-12 22:03:12.921 I/MSM-irqbalance( 1927): Decided to move IRQ3 from CPU2 [P:0] to CPU7 [P:1] (banned)
05-12 22:03:12.922 I/MSM-irqbalance( 1927): Decided to move IRQ5 from CPU2 [P:0] to CPU5 [P:1] (banned)
05-12 22:03:12.922 I/MSM-irqbalance( 1927): Decided to move IRQ3 from CPU3 [P:0] to CPU6 [P:1] (banned)
05-12 22:03:12.922 I/MSM-irqbalance( 1927): Decided to move IRQ5 from CPU3 [P:0] to CPU4 [P:1] (banned)
05-12 22:03:18.241 I/MSM-irqbalance( 1927): Decided to move IRQ5 from CPU2 [P:0] to CPU7 [P:1] (banned)
05-12 22:03:18.241 I/MSM-irqbalance( 1927): Decided to move IRQ5 from CPU3 [P:0] to CPU5 [P:1] (banned)
05-12 22:03:20.421 E/IzatSvc_OSObserver( 2310): I/LocTech-Label :: OSOBSERVER :: Data Items In
05-12 22:03:20.421 E/IzatSvc_OSObserver( 2310): I/LocTech-Value :: Data Item Value: Attach state: 3, Mac address valid: false, AP MAC address: [00:00:00:00:00:00], Wifi-Ap SSID Valid: false, SSID:
05-12 22:03:23.180 E/IzatSvc_Wiper( 2310): W/Num of elements returned by LOWI 20
05-12 22:03:23.181 E/LocSvc_api_v02( 2310): I/---> locClientSendReq line 2069 QMI_LOC_INJECT_WIFI_POSITION_REQ_V02
05-12 22:03:23.190 W/XTCC-5.1.0.23( 2353): [LOWIUtils] to_eScanTypeResponse - default case
05-12 22:03:23.190 W/XTCC-5.1.0.23( 2353): [WifiScanner] WiFi scan result : [20] AP's
05-12 22:03:23.191 E/LocSvc_ApiV02( 2310): I/<--- void globalRespCb(locClientHandleType, uint32_t, const locClientRespIndUnionType, uint32_t, void *) line 140 QMI_LOC_INJECT_WIFI_POSITION_REQ_V02
05-12 22:03:23.191 E/IzatSvc_Wiper( 2310): W/Num of elements returned by LOWI 20
05-12 22:03:23.191 E/LocSvc_api_v02( 2310): I/---> locClientSendReq line 2069 QMI_LOC_INJECT_WIFI_POSITION_REQ_V02
05-12 22:03:23.192 E/LocSvc_ApiV02( 2310): I/<--- void globalRespCb(locClientHandleType, uint32_t, const locClientRespIndUnionType, uint32_t, void *) line 140 QMI_LOC_INJECT_WIFI_POSITION_REQ_V02
05-12 22:03:23.216 E/IzatSvc_OSObserver( 2310): I/LocTech-Label :: OSOBSERVER :: Data Items In
05-12 22:03:23.217 E/IzatSvc_OSObserver( 2310): I/LocTech-Value :: Data Item Value: Attach state: 0, Mac address valid: false, AP MAC address: [00:00:00:00:00:00], Wifi-Ap SSID Valid: false, SSID:
05-12 22:03:23.222 D/WifiQualifiedNetworkSelector:( 2310): ==========start qualified Network Selection==========
05-12 22:03:23.223 D/WifiQualifiedNetworkSelector:( 2310): Saved Network List
05-12 22:03:23.223 D/WifiQualifiedNetworkSelector:( 2310): "2044411083":0 User Preferred BSSID:null FQDN:ngh.pirosap.tech NETWORK_SELECTION_ENABLED Disable account: 0 0 0 0 0 0 0 0 0 0 Connect Choice:null set time:-1
05-12 22:03:23.224 D/HS20 ( 2310): match nwk 'aruba-HS20':24dec6ca5378 (020824dec6ca), anqp present, query true, home sps: 1
05-12 22:03:23.224 D/HS20 ( 2310): 'aruba-HS20':24dec6ca5378 (020824dec6ca) match on ngh.pirosap.tech: HomeProvider, auth RealmMethodParam
05-12 22:03:23.224 D/HS20 ( 2310): -- ngh.pirosap.tech: match HomeProvider, queried false
05-12 22:03:23.224 D/HS20 ( 2310): aruba-HS20 pass 1 matches: ngh.pirosap.tech->HomeProvider
05-12 22:03:23.226 D/HS20 ( 2310): match nwk 'aruba-HS20':24dec6ca5370 (020824dec6ca), anqp missing, query true, home sps: 1
05-12 22:03:23.227 D/HS20 ( 2310): -- ngh.pirosap.tech: match Incomplete, queried false
05-12 22:03:23.228 I/wpa_supplicant( 2831): wlan0: GAS-QUERY-START addr=24:de:c6:ca:53:70 dialog_token=29 freq=2462
05-12 22:03:23.230 D/HS20 ( 2310): ANQP initiated on 'aruba-HS20'/24dec6ca5370 (ANQP_GET 24:de:c6:ca:53:70 258,260,262,263,264,268,hs20:3,hs20:4,hs20:5)
05-12 22:03:23.230 D/HS20 ( 2310): aruba-HS20 pass 1 matches: ngh.pirosap.tech->Incomplete
05-12 22:03:23.231 D/HS20 ( 2310): match nwk 'Meraki-HS20':e2557de88042 (020800000000), anqp missing, query true, home sps: 1
05-12 22:03:23.231 D/HS20 ( 2310): -- ngh.pirosap.tech: match Incomplete, queried false
05-12 22:03:23.240 I/MSM-irqbalance( 1927): Decided to move IRQ5 from CPU2 [P:0] to CPU7 [P:1] (banned)
05-12 22:03:23.247 I/wpa_supplicant( 2831): wlan0: GAS-QUERY-START addr=e2:55:7d:e8:80:42 dialog_token=30 freq=2412
05-12 22:03:23.248 D/HS20 ( 2310): ANQP initiated on 'Meraki-HS20'/e2557de88042 (ANQP_GET e2:55:7d:e8:80:42 258,260,262,263,264,268,hs20:3,hs20:4,hs20:5)
05-12 22:03:23.248 D/HS20 ( 2310): Meraki-HS20 pass 1 matches: ngh.pirosap.tech->Incomplete
05-12 22:03:23.250 D/HS20 ( 2310): match nwk 'Meraki-HS20':e2556de88042 (020800000000), anqp missing, query true, home sps: 1
05-12 22:03:23.251 D/HS20 ( 2310): -- ngh.pirosap.tech: match Incomplete, queried false
05-12 22:03:23.258 I/wpa_supplicant( 2831): wlan0: GAS-QUERY-START addr=e2:55:6d:e8:80:42 dialog_token=31 freq=5220
05-12 22:03:23.259 D/HS20 ( 2310): ANQP initiated on 'Meraki-HS20'/e2556de88042 (ANQP_GET e2:55:6d:e8:80:42 258,260,262,263,264,268,hs20:3,hs20:4,hs20:5)
05-12 22:03:23.259 D/HS20 ( 2310): Meraki-HS20 pass 1 matches: ngh.pirosap.tech->Incomplete
05-12 22:03:23.260 D/WifiQualifiedNetworkSelector:( 2310): Guest28154:36:76:c5:48:6d:fa(2.4GHz)-87 / AirPort28154:34:76:c5:4a:6d:fa(2.4GHz)-87 / skipped due to low signal
05-12 22:03:23.260 D/WifiQualifiedNetworkSelector:( 2310): aruba-HS20:24:de:c6:ca:53:70 / Meraki-HS20:e2:55:7d:e8:80:42 / puyo:e2:55:7d:e8:80:41 / hoge:e2:55:7d:e8:80:40 / DIRECT-Ub-BRAVIA:b2:10:41:36:c6:df / WARPSTAR-E391D5:00:3a:9d:67:0a:b5 / aterm-781629-g:c0:25:a2:5d:fa:86 / WARPSTAR-E391D5-W:06:3a:9d:67:0a:b5 / puyo:e2:55:6d:e8:80:41 / hoge:e2:55:6d:e8:80:40 / Meraki-HS20:e2:55:6d:e8:80:42 / Buffalo-G-7DD8:34:3d:c4:4e:7d:d8 / Game32364:00:a0:b0:b3:7e:6e / Stream32364:00:a0:b0:b3:7e:6d / skipped due to not saved
05-12 22:03:23.260 D/WifiQualifiedNetworkSelector:( 2310):
05-12 22:03:23.260 D/WifiQualifiedNetworkSelector:( 2310): e2:55:6d:e8:80:4f / e2:55:7d:e8:80:40 / e2:55:7d:e8:80:42 / skipped due to not valid SSID
05-12 22:03:23.261 D/WifiQualifiedNetworkSelector:( 2310): RSSI score: 100 5GHz bonus: 40 Passpoint Bonus:40 Score for scanResult: SSID: aruba-HS20, BSSID: 24:de:c6:ca:53:78, capabilities: [WPA2-EAP-CCMP][ESS][P2P][HS20], level: -51, frequency: 5260, timestamp: 4679781268, distance: ?(cm), distanceSd: ?(cm), passpoint: no, ChannelBandwidth: 1, centerFreq0: 5270, centerFreq1: 0, 80211mcResponder: is not supported and Network ID: 0 final score:180
05-12 22:03:23.261 D/WifiQualifiedNetworkSelector:( 2310):
05-12 22:03:23.261 D/WifiQualifiedNetworkSelector:( 2310): After user choice adjust, the final candidate is:"2044411083":0 : 24:de:c6:ca:53:78
05-12 22:03:23.261 D/WifiQualifiedNetworkSelector:( 2310): reconnect from Disconnected to "2044411083":0
05-12 22:03:23.262 D/WifiStateMachine( 2310): CMD_AUTO_CONNECT sup state DisconnectedState my state DisconnectedState nid=0 roam=false
05-12 22:03:23.262 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.263 D/WifiStateMachine( 2310): CMD_AUTO_CONNECT will save config -> "aruba-HS20" nid=0
05-12 22:03:23.265 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.266 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.267 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.268 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.269 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.269 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.270 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.271 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.272 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.273 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.274 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.274 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.275 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.276 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.277 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.278 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.278 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.279 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.280 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.281 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.282 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.282 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.284 D/WifiConfigManager( 2310): created a homeSP object for 0:"aruba-HS20"
05-12 22:03:23.293 D/HS20 ( 2310): Adding or updating HS20 profile for ngh.pirosap.tech
05-12 22:03:23.312 D/WifiNetworkHistory( 2310): saving network history: ngh.pirosap.techWPA_EAP gw: null Network Selection-status: NETWORK_SELECTION_ENABLED ephemeral=false choice:null link:0 status:0 nid:0 hasEverConnected: false
05-12 22:03:23.312 V/WifiNetworkHistory( 2310): writeKnownNetworkHistory write config ngh.pirosap.techWPA_EAP
05-12 22:03:23.324 D/WifiStateMachine( 2310): CMD_AUTO_CONNECT did save config -> nid=0
05-12 22:03:23.324 D/WifiConfigManager( 2310): Setting SSID for 0 toaruba-HS20
05-12 22:03:23.325 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:23.328 E/wpa_supplicant( 2831): eap_proxy: eap_proxy_notify_config
05-12 22:03:23.330 D/WifiNetworkHistory( 2310): saving network history: ngh.pirosap.techWPA_EAP gw: null Network Selection-status: NETWORK_SELECTION_ENABLED ephemeral=false choice:null link:0 status:0 nid:0 hasEverConnected: false
05-12 22:03:23.330 V/WifiNetworkHistory( 2310): writeKnownNetworkHistory write config ngh.pirosap.techWPA_EAP
05-12 22:03:23.800 I/wpa_supplicant( 2831): wlan0: GAS-QUERY-DONE addr=24:de:c6:ca:53:70 dialog_token=29 freq=2462 status_code=0 result=SUCCESS
05-12 22:03:23.811 I/wpa_supplicant( 2831): wlan0: RX-ANQP 24:de:c6:ca:53:70 Venue Name
05-12 22:03:23.811 I/wpa_supplicant( 2831): wlan0: RX-ANQP 24:de:c6:ca:53:70 Network Authentication Type information
05-12 22:03:23.811 I/wpa_supplicant( 2831): wlan0: RX-ANQP 24:de:c6:ca:53:70 IP Address Type Availability information
05-12 22:03:23.811 I/wpa_supplicant( 2831): wlan0: RX-ANQP 24:de:c6:ca:53:70 NAI Realm list
05-12 22:03:23.811 I/wpa_supplicant( 2831): wlan0: RX-ANQP 24:de:c6:ca:53:70 3GPP Cellular Network information
05-12 22:03:23.811 I/wpa_supplicant( 2831): wlan0: RX-ANQP 24:de:c6:ca:53:70 Domain Name list
05-12 22:03:23.811 I/wpa_supplicant( 2831): wlan0: RX-HS20-ANQP 24:de:c6:ca:53:70 Operator Friendly Name
05-12 22:03:23.811 I/wpa_supplicant( 2831): wlan0: RX-HS20-ANQP 24:de:c6:ca:53:70 Connection Capability
05-12 22:03:23.811 I/wpa_supplicant( 2831): wlan0: ANQP-QUERY-DONE addr=24:de:c6:ca:53:70 result=SUCCESS
05-12 22:03:23.812 I/wpa_supplicant( 2831): wlan0: Trying to associate with SSID 'aruba-HS20'
05-12 22:03:23.816 E/wpa_supplicant( 2831): eap_proxy: eap_proxy_notify_config
05-12 22:03:23.816 E/wpa_supplicant( 2831): eap_proxy: eap_proxy_allowed_method
05-12 22:03:23.816 E/wpa_supplicant( 2831): eap_proxy: eap_proxy_allowed_method
05-12 22:03:23.816 E/wpa_supplicant( 2831): eap_proxy: eap_proxy_allowed_method
05-12 22:03:23.822 D/HS20 ( 2310): successful ANQP response for 24dec6ca5370: {ANQPIPAddrAvailability=IPAddressTypeAvailability{mV4Availability=Public, mV6Availability=NotAvailable}, ANQPNAIRealm=NAI Realm:
05-12 22:03:23.822 D/HS20 ( 2310): NAI Realm(s) pirosap.tech
05-12 22:03:23.822 D/HS20 ( 2310): EAP Method EAP_TTLS
05-12 22:03:23.822 D/HS20 ( 2310): Auth method NonEAPInnerAuthEAP, inner = MSCHAPv2
05-12 22:03:23.822 D/HS20 ( 2310): Auth method CredentialType = Username
05-12 22:03:23.822 D/HS20 ( 2310): , ANQPVenueName=VenueName{m_group=Unspecified, m_type=Unspecified, m_names=[]}, ANQPDomName=DomainName{mDomains=[ngh.pirosap.tech, nttdocomo.com]}, ANQPNwkAuthType=NetworkAuthenticationType{m_authenticationTypes=[]}, HSConnCapability=HSConnectionCapability{mStatusList=[]}, ANQP3GPPNetwork=ThreeGPPNetwork{mUserData=0, mPlmns=[PLMN: 44010 44051 440209 440209 440001]}, HSFriendlyName=HSFriendlyName{mNames=[]}}
05-12 22:03:23.823 D/HS20 ( 2310): match nwk 'aruba-HS20':24dec6ca5370 (020824dec6ca), anqp present, query false, home sps: 1
05-12 22:03:23.823 D/HS20 ( 2310): 'aruba-HS20':24dec6ca5370 (020824dec6ca) match on ngh.pirosap.tech: HomeProvider, auth RealmMethodParam
05-12 22:03:23.823 D/HS20 ( 2310): -- ngh.pirosap.tech: match HomeProvider, queried true
05-12 22:03:23.823 D/HS20 ( 2310): aruba-HS20 pass 2 matches: ngh.pirosap.tech->HomeProvider
05-12 22:03:23.832 E/IzatSvc_OSObserver( 2310): I/LocTech-Label :: OSOBSERVER :: Data Items In
05-12 22:03:23.832 E/IzatSvc_OSObserver( 2310): I/LocTech-Value :: Data Item Value: Attach state: 5, Mac address valid: false, AP MAC address: [00:00:00:00:00:00], Wifi-Ap SSID Valid: false, SSID:
05-12 22:03:23.950 I/QtiTetherService/TetherNotifier( 3175): Active=[]; Available=[wlan0]; Errored=[]
05-12 22:03:23.951 I/QtiTetherService/TetherCommunication( 3175): Posting: TetherEvent -- TetherStateChangedEvent{Active=[], Available=[wlan0], Errored=[]}
05-12 22:03:23.951 I/QtiTetherService( 3175): handleMessage(TetherEvent -- TetherStateChangedEvent{Active=[], Available=[wlan0], Errored=[]})
05-12 22:03:23.960 I/TetherStatsReporting( 2310): getTetherStats() called NetworkStats: elapsedRealtime=4680567
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [0] iface=wlan0 uid=0 set=DEFAULT tag=0x0 roaming=NO rxBytes=54742 rxPackets=447 txBytes=29680 txPackets=461 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [1] iface=wlan0 uid=0 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [2] iface=wlan0 uid=1000 set=DEFAULT tag=0x0 roaming=NO rxBytes=4372 rxPackets=44 txBytes=7677 txPackets=60 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [3] iface=wlan0 uid=1000 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [4] iface=wlan0 uid=10011 set=DEFAULT tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=144 txPackets=2 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [5] iface=wlan0 uid=10011 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [6] iface=wlan0 uid=10013 set=DEFAULT tag=0x0 roaming=NO rxBytes=34750 rxPackets=136 txBytes=81931 txPackets=168 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [7] iface=wlan0 uid=10013 set=FOREGROUND tag=0x0 roaming=NO rxBytes=40714 rxPackets=111 txBytes=98807 txPackets=150 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [8] iface=wlan0 uid=10036 set=DEFAULT tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [9] iface=wlan0 uid=10036 set=FOREGROUND tag=0x0 roaming=NO rxBytes=40758 rxPackets=38 txBytes=2572 txPackets=23 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [10] iface=wlan0 uid=10059 set=DEFAULT tag=0x0 roaming=NO rxBytes=16393378 rxPackets=13143 txBytes=475801 txPackets=6587 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [11] iface=wlan0 uid=10059 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [12] iface=wlan0 uid=10062 set=DEFAULT tag=0x0 roaming=NO rxBytes=6094 rxPackets=11 txBytes=1426 txPackets=11 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [13] iface=wlan0 uid=10062 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [14] iface=wlan0 uid=10063 set=DEFAULT tag=0x0 roaming=NO rxBytes=14410 rxPackets=66 txBytes=10290 txPackets=85 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [15] iface=wlan0 uid=10063 set=FOREGROUND tag=0x0 roaming=NO rxBytes=2495802 rxPackets=2865 txBytes=650496 txPackets=2694 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [16] iface=wlan0 uid=10086 set=DEFAULT tag=0x0 roaming=NO rxBytes=5876 rxPackets=12 txBytes=2333 txPackets=11 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [17] iface=wlan0 uid=10086 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [18] iface=wlan0 uid=10088 set=DEFAULT tag=0x0 roaming=NO rxBytes=10832 rxPackets=32 txBytes=6307 txPackets=38 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [19] iface=wlan0 uid=10088 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [20] iface=wlan0 uid=10013 set=DEFAULT tag=0x600 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [21] iface=wlan0 uid=10013 set=FOREGROUND tag=0x600 roaming=NO rxBytes=5112 rxPackets=11 txBytes=2349 txPackets=11 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [22] iface=wlan0 uid=10036 set=DEFAULT tag=0x600 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [23] iface=wlan0 uid=10036 set=FOREGROUND tag=0x600 roaming=NO rxBytes=40758 rxPackets=38 txBytes=2572 txPackets=23 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [24] iface=wlan0 uid=10013 set=DEFAULT tag=0x10000407 roaming=NO rxBytes=1103 rxPackets=9 txBytes=939 txPackets=7 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [25] iface=wlan0 uid=10013 set=FOREGROUND tag=0x10000407 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [26] iface=wlan0 uid=10013 set=DEFAULT tag=0x10001301 roaming=NO rxBytes=9400 rxPackets=16 txBytes=2977 txPackets=17 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [27] iface=wlan0 uid=10013 set=FOREGROUND tag=0x10001301 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [28] iface=wlan0 uid=10013 set=DEFAULT tag=0x20000407 roaming=NO rxBytes=5829 rxPackets=14 txBytes=3943 txPackets=13 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [29] iface=wlan0 uid=10013 set=FOREGROUND tag=0x20000407 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [30] iface=wlan0 uid=10013 set=DEFAULT tag=0x21065fff roaming=NO rxBytes=8662 rxPackets=30 txBytes=24691 txPackets=31 operations=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): [31] iface=wlan0 uid=10013 set=FOREGROUND tag=0x21065fff roaming=NO rxBytes=0 rxPackets=0 txBytes=0
05-12 22:03:23.960 I/TetherStatsReporting( 2310): combining tether stats
05-12 22:03:23.962 D/QtiTetherService/IpaWrapper( 3175): getStats(false)
05-12 22:03:23.998 I/wpa_supplicant( 2831): wlan0: Associated with 24:de:c6:ca:53:78
05-12 22:03:23.998 I/wpa_supplicant( 2831): wlan0: CTRL-EVENT-SUBNET-STATUS-UPDATE status=0
05-12 22:03:23.999 I/wpa_supplicant( 2831): wlan0: CTRL-EVENT-EAP-STARTED EAP authentication started
05-12 22:03:24.006 I/WifiHAL ( 2310): Unknown EAPOL message type
05-12 22:03:24.006 I/wpa_supplicant( 2831): wlan0: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=21
05-12 22:03:24.007 E/IzatSvc_OSObserver( 2310): I/LocTech-Label :: OSOBSERVER :: Data Items In
05-12 22:03:24.007 E/IzatSvc_OSObserver( 2310): I/LocTech-Value :: Data Item Value: Attach state: 6, Mac address valid: false, AP MAC address: [00:00:00:00:00:00], Wifi-Ap SSID Valid: false, SSID:
05-12 22:03:24.009 I/wpa_supplicant( 2831): wlan0: CTRL-EVENT-EAP-METHOD EAP vendor 0 method 21 (TTLS) selected
05-12 22:03:24.010 I/WifiHAL ( 2310): Unknown EAPOL message type
05-12 22:03:24.023 E/IzatSvc_Wiper( 2310): W/Num of elements returned by LOWI 20
05-12 22:03:24.024 E/LocSvc_api_v02( 2310): I/---> locClientSendReq line 2069 QMI_LOC_INJECT_WIFI_POSITION_REQ_V02
05-12 22:03:24.024 W/XTCC-5.1.0.23( 2353): [LOWIUtils] to_eScanTypeResponse - default case
05-12 22:03:24.024 W/XTCC-5.1.0.23( 2353): [WifiScanner] WiFi scan result : [20] AP's
05-12 22:03:24.026 E/LocSvc_ApiV02( 2310): I/<--- void globalRespCb(locClientHandleType, uint32_t, const locClientRespIndUnionType, uint32_t, void *) line 140 QMI_LOC_INJECT_WIFI_POSITION_REQ_V02
05-12 22:03:24.052 I/WifiHAL ( 2310): Unknown EAPOL message type
05-12 22:03:24.052 I/WifiHAL ( 2310): Unknown EAPOL message type
05-12 22:03:24.075 I/WifiHAL ( 2310): Unknown EAPOL message type
05-12 22:03:24.077 I/wpa_supplicant( 2831): wlan0: CTRL-EVENT-EAP-PEER-CERT depth=2 subject='/O=Digital Signature Trust Co./CN=DST Root CA X3' hash=0687260331a72403d909f105e69bcf0d32e1bd2493ffc6d9206d11bcd6770739
05-12 22:03:24.079 I/wpa_supplicant( 2831): wlan0: CTRL-EVENT-EAP-PEER-CERT depth=1 subject='/C=US/O=Let's Encrypt/CN=Let's Encrypt Authority X3' hash=25847d668eb4f04fdd40b12b6b0740c567da7d024308eb6c2c96fe41d9de218d
05-12 22:03:24.082 I/wpa_supplicant( 2831): wlan0: CTRL-EVENT-EAP-PEER-CERT depth=0 subject='/CN=ngh.pirosap.tech' hash=ab8e3a9ddc421f8ec984cd222ce5aecdc09e3b5bffaedc3df8946aec12006c74
05-12 22:03:24.085 I/wpa_supplicant( 2831): wlan0: CTRL-EVENT-EAP-PEER-ALT depth=0 DNS:ngh.pirosap.tech
05-12 22:03:24.089 I/WifiHAL ( 2310): Unknown EAPOL message type
05-12 22:03:24.114 I/WifiHAL ( 2310): Unknown EAPOL message type
05-12 22:03:24.114 I/wpa_supplicant( 2831): EAP-TTLS: Phase 2 MSCHAPV2 authentication succeeded
05-12 22:03:24.115 I/WifiHAL ( 2310): Unknown EAPOL message type
05-12 22:03:24.123 I/WifiHAL ( 2310): Unknown EAPOL message type
05-12 22:03:24.123 I/wpa_supplicant( 2831): wlan0: CTRL-EVENT-EAP-SUCCESS EAP authentication completed successfully
05-12 22:03:24.132 E/IzatSvc_OSObserver( 2310): I/LocTech-Label :: OSOBSERVER :: Data Items In
05-12 22:03:24.132 E/IzatSvc_OSObserver( 2310): I/LocTech-Value :: Data Item Value: Attach state: 7, Mac address valid: false, AP MAC address: [00:00:00:00:00:00], Wifi-Ap SSID Valid: false, SSID:
05-12 22:03:24.139 E/wpa_supplicant( 2831): WPS: wpas_wps_eapol_cb cancel timeout
05-12 22:03:24.140 I/wpa_supplicant( 2831): wlan0: WPA: Key negotiation completed with 24:de:c6:ca:53:78 [PTK=CCMP GTK=CCMP]
05-12 22:03:24.140 I/wpa_supplicant( 2831): wlan0: CTRL-EVENT-CONNECTED - Connection to 24:de:c6:ca:53:78 completed [id=0 id_str=%7B%22creatorUid%22%3A%2210042%22%2C%22configKey%22%3A%22ngh.pirosap.techWPA_EAP%22%2C%22fqdn%22%3A%22ngh.pirosap.tech%22%7D]
05-12 22:03:24.145 E/IzatSvc_OSObserver( 2310): I/LocTech-Label :: OSOBSERVER :: Data Items In
05-12 22:03:24.146 E/IzatSvc_OSObserver( 2310): I/LocTech-Value :: Data Item Value: Attach state: 8, Mac address valid: false, AP MAC address: [00:00:00:00:00:00], Wifi-Ap SSID Valid: false, SSID:
05-12 22:03:24.150 E/WifiScanner( 2310): listener cannot be found
05-12 22:03:24.155 D/ConnectivityService( 2310): registerNetworkAgent NetworkAgentInfo{ ni{[type: WIFI[], state: CONNECTING/CONNECTING, reason: (unspecified), extra: "aruba-HS20", failover: false, available: true, roaming: false, metered: false]} network{107} nethandle{459577936606} lp{{LinkAddresses: [] Routes: [] DnsAddresses: [] Domains: null MTU: 0}} nc{[ Transports: WIFI Capabilities: NOT_METERED&INTERNET&NOT_RESTRICTED&TRUSTED&NOT_VPN LinkUpBandwidth>=1048576Kbps LinkDnBandwidth>=1048576Kbps]} Score{20} everValidated{false} lastValidated{false} created{false} lingering{false} explicitlySelected{false} acceptUnvalidated{false} everCaptivePortalDetected{false} lastCaptivePortalDetected{false} }
05-12 22:03:24.155 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:24.155 D/ConnectivityService( 2310): NetworkAgentInfo [WIFI () - 107] EVENT_NETWORK_INFO_CHANGED, going from null to CONNECTING
05-12 22:03:24.158 E/wifi_gbk2utf( 2310): g_pItemList is NULL
05-12 22:03:24.167 E/WifiHAL ( 2310): wifi_get_packet_filter_capabilities: requestResponse() error: -95
05-12 22:03:24.167 I/WifiHAL ( 2310): Packet filtering is not supprted
05-12 22:03:24.167 D/wifi ( 2310): APF version supported: 0
05-12 22:03:24.167 D/wifi ( 2310): Maximum APF program size: 0
05-12 22:03:24.169 D/WifiStateMachine( 2310): Start Dhcp Watchdog 4
05-12 22:03:24.179 I/cnss-daemon( 1818): RTM_NEWROUTE Indication
05-12 22:03:24.179 I/cnss-daemon( 1818): RTM_NEWROUTE Indication
05-12 22:03:24.179 D/ScanDetailCache( 2310): Visiblity by passpoint match returned 5 GHz BSSID of 24:de:c6:ca:53:78
05-12 22:03:24.180 I/cnss-daemon( 1818): RTM_NEWROUTE Indication
05-12 22:03:24.182 D/WifiNative-wlan0( 2310): configureNeighborDiscoveryOffload(true)
05-12 22:03:24.182 D/WifiNative-wlan0( 2310): configureNeighborDiscoveryOffload(true) returned: -95
05-12 22:03:24.188 E/IzatSvc_OSObserver( 2310): I/LocTech-Label :: OSOBSERVER :: Data Items In
05-12 22:03:24.188 E/IzatSvc_OSObserver( 2310): I/LocTech-Value :: Data Item Value: Attach state: 9, Mac address valid: true, AP MAC address: [24:de:c6:ca:53:78], Wifi-Ap SSID Valid: true, SSID: aruba-HS20
05-12 22:03:24.191 E/LocSvc_api_v02( 2310): I/---> locClientSendReq line 2069 QMI_LOC_NOTIFY_WIFI_ATTACHMENT_STATUS_REQ_V02
05-12 22:03:24.193 E/LocSvc_ApiV02( 2310): I/<--- void globalRespCb(locClientHandleType, uint32_t, const locClientRespIndUnionType, uint32_t, void *) line 140 QMI_LOC_NOTIFY_WIFI_ATTACHMENT_STATUS_REQ_V02
05-12 22:03:24.259 D/DhcpClient( 2310): Receive thread started
05-12 22:03:24.264 D/DhcpClient( 2310): Broadcasting DHCPDISCOVER
05-12 22:03:24.272 D/DhcpClient( 2310): Received packet: cc:9f:7a:01:2b:22 OFFER, ip /172.31.0.9, mask /255.255.255.0, DNS servers: /172.31.0.1 , gateways [/172.31.0.1] lease time 86400, domain null
05-12 22:03:24.273 D/DhcpClient( 2310): Got pending lease: IP address 172.31.0.9/24 Gateway 172.31.0.1 DNS servers: [ 172.31.0.1 ] Domains DHCP server /172.31.0.1 Vendor info null lease 86400 seconds
05-12 22:03:24.275 D/DhcpClient( 2310): Broadcasting DHCPREQUEST ciaddr=0.0.0.0 request=172.31.0.9 serverid=172.31.0.1
05-12 22:03:24.279 D/DhcpClient( 2310): Received packet: cc:9f:7a:01:2b:22 ACK: your new IP /172.31.0.9, netmask /255.255.255.0, gateways [/172.31.0.1] DNS servers: /172.31.0.1 , lease time 86400
05-12 22:03:24.280 D/DhcpClient( 2310): Confirmed lease: IP address 172.31.0.9/24 Gateway 172.31.0.1 DNS servers: [ 172.31.0.1 ] Domains DHCP server /172.31.0.1 Vendor info null lease 86400 seconds
05-12 22:03:24.288 D/CommandListener( 1816): Setting iface cfg
05-12 22:03:24.307 I/cnss-daemon( 1818): RTM_NEWROUTE Indication
05-12 22:03:24.308 I/cnss-daemon( 1818): RTM_NEWROUTE Indication
05-12 22:03:24.308 I/cnss-daemon( 1818): RTM_NEWROUTE Indication
05-12 22:03:24.308 I/cnss-daemon( 1818): RTM_NEWROUTE Indication
05-12 22:03:24.315 E/WifiNative-HAL( 2310): setBssidBlacklist cmd 3 size 0
05-12 22:03:24.315 D/wifi ( 2310): configure BSSID black list request [4] = 0x7f7fc8ffa0
05-12 22:03:24.315 D/wifi ( 2310): Added 0 bssids
05-12 22:03:24.315 E/WifiHAL ( 2310): wifi_set_bssid_blacklist(): requestResponse Error:-95
05-12 22:03:24.317 D/DhcpClient( 2310): Scheduling renewal in 43199s
05-12 22:03:24.317 D/DhcpClient( 2310): Scheduling rebind in 75599s
05-12 22:03:24.317 D/DhcpClient( 2310): Scheduling expiry in 86399s
05-12 22:03:24.318 D/ConnectivityService( 2310): NetworkAgentInfo [WIFI () - 107] EVENT_NETWORK_INFO_CHANGED, going from CONNECTING to CONNECTED
05-12 22:03:24.320 D/ConnectivityService( 2310): Adding iface wlan0 to network 107
05-12 22:03:24.358 E/WifiStateMachine( 2310): Did not find remoteAddress {172.31.0.1} in /proc/net/arp
05-12 22:03:24.397 I/cnss-daemon( 1818): RTM_NEWROUTE Indication
05-12 22:03:24.399 I/cnss-daemon( 1818): RTM_NEWROUTE Indication
05-12 22:03:24.401 I/cnss-daemon( 1818): RTM_NEWROUTE Indication
05-12 22:03:24.401 I/cnss-daemon( 1818): ip type is ipv4
05-12 22:03:24.402 D/ConnectivityService( 2310): Setting DNS servers for network 107 to [/172.31.0.1]
05-12 22:03:24.416 I/TetherStatsReporting( 2310): getTetherStats() called NetworkStats: elapsedRealtime=4681024
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [0] iface=wlan0 uid=0 set=DEFAULT tag=0x0 roaming=NO rxBytes=54742 rxPackets=447 txBytes=29896 txPackets=464 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [1] iface=wlan0 uid=0 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [2] iface=wlan0 uid=1000 set=DEFAULT tag=0x0 roaming=NO rxBytes=4372 rxPackets=44 txBytes=7677 txPackets=60 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [3] iface=wlan0 uid=1000 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [4] iface=wlan0 uid=10011 set=DEFAULT tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=144 txPackets=2 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [5] iface=wlan0 uid=10011 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [6] iface=wlan0 uid=10013 set=DEFAULT tag=0x0 roaming=NO rxBytes=34750 rxPackets=136 txBytes=81931 txPackets=168 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [7] iface=wlan0 uid=10013 set=FOREGROUND tag=0x0 roaming=NO rxBytes=40714 rxPackets=111 txBytes=98807 txPackets=150 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [8] iface=wlan0 uid=10036 set=DEFAULT tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [9] iface=wlan0 uid=10036 set=FOREGROUND tag=0x0 roaming=NO rxBytes=40758 rxPackets=38 txBytes=2572 txPackets=23 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [10] iface=wlan0 uid=10059 set=DEFAULT tag=0x0 roaming=NO rxBytes=16393378 rxPackets=13143 txBytes=475801 txPackets=6587 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [11] iface=wlan0 uid=10059 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [12] iface=wlan0 uid=10062 set=DEFAULT tag=0x0 roaming=NO rxBytes=6094 rxPackets=11 txBytes=1426 txPackets=11 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [13] iface=wlan0 uid=10062 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [14] iface=wlan0 uid=10063 set=DEFAULT tag=0x0 roaming=NO rxBytes=14410 rxPackets=66 txBytes=10290 txPackets=85 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [15] iface=wlan0 uid=10063 set=FOREGROUND tag=0x0 roaming=NO rxBytes=2495802 rxPackets=2865 txBytes=650496 txPackets=2694 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [16] iface=wlan0 uid=10086 set=DEFAULT tag=0x0 roaming=NO rxBytes=5876 rxPackets=12 txBytes=2333 txPackets=11 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [17] iface=wlan0 uid=10086 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [18] iface=wlan0 uid=10088 set=DEFAULT tag=0x0 roaming=NO rxBytes=10832 rxPackets=32 txBytes=6307 txPackets=38 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [19] iface=wlan0 uid=10088 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [20] iface=wlan0 uid=10013 set=DEFAULT tag=0x600 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [21] iface=wlan0 uid=10013 set=FOREGROUND tag=0x600 roaming=NO rxBytes=5112 rxPackets=11 txBytes=2349 txPackets=11 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [22] iface=wlan0 uid=10036 set=DEFAULT tag=0x600 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [23] iface=wlan0 uid=10036 set=FOREGROUND tag=0x600 roaming=NO rxBytes=40758 rxPackets=38 txBytes=2572 txPackets=23 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [24] iface=wlan0 uid=10013 set=DEFAULT tag=0x10000407 roaming=NO rxBytes=1103 rxPackets=9 txBytes=939 txPackets=7 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [25] iface=wlan0 uid=10013 set=FOREGROUND tag=0x10000407 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [26] iface=wlan0 uid=10013 set=DEFAULT tag=0x10001301 roaming=NO rxBytes=9400 rxPackets=16 txBytes=2977 txPackets=17 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [27] iface=wlan0 uid=10013 set=FOREGROUND tag=0x10001301 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [28] iface=wlan0 uid=10013 set=DEFAULT tag=0x20000407 roaming=NO rxBytes=5829 rxPackets=14 txBytes=3943 txPackets=13 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [29] iface=wlan0 uid=10013 set=FOREGROUND tag=0x20000407 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [30] iface=wlan0 uid=10013 set=DEFAULT tag=0x21065fff roaming=NO rxBytes=8662 rxPackets=30 txBytes=24691 txPackets=31 operations=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): [31] iface=wlan0 uid=10013 set=FOREGROUND tag=0x21065fff roaming=NO rxBytes=0 rxPackets=0 txBytes=0
05-12 22:03:24.416 I/TetherStatsReporting( 2310): combining tether stats
05-12 22:03:24.417 D/QtiTetherService/IpaWrapper( 3175): getStats(false)
05-12 22:03:24.430 I/TetherStatsReporting( 2310): getTetherStats() called NetworkStats: elapsedRealtime=4681038
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [0] iface=wlan0 uid=0 set=DEFAULT tag=0x0 roaming=NO rxBytes=54742 rxPackets=447 txBytes=29896 txPackets=464 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [1] iface=wlan0 uid=0 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [2] iface=wlan0 uid=1000 set=DEFAULT tag=0x0 roaming=NO rxBytes=4372 rxPackets=44 txBytes=7677 txPackets=60 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [3] iface=wlan0 uid=1000 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [4] iface=wlan0 uid=10011 set=DEFAULT tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=144 txPackets=2 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [5] iface=wlan0 uid=10011 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [6] iface=wlan0 uid=10013 set=DEFAULT tag=0x0 roaming=NO rxBytes=34750 rxPackets=136 txBytes=81931 txPackets=168 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [7] iface=wlan0 uid=10013 set=FOREGROUND tag=0x0 roaming=NO rxBytes=40714 rxPackets=111 txBytes=98807 txPackets=150 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [8] iface=wlan0 uid=10036 set=DEFAULT tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [9] iface=wlan0 uid=10036 set=FOREGROUND tag=0x0 roaming=NO rxBytes=40758 rxPackets=38 txBytes=2572 txPackets=23 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [10] iface=wlan0 uid=10059 set=DEFAULT tag=0x0 roaming=NO rxBytes=16393378 rxPackets=13143 txBytes=475801 txPackets=6587 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [11] iface=wlan0 uid=10059 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [12] iface=wlan0 uid=10062 set=DEFAULT tag=0x0 roaming=NO rxBytes=6094 rxPackets=11 txBytes=1426 txPackets=11 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [13] iface=wlan0 uid=10062 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [14] iface=wlan0 uid=10063 set=DEFAULT tag=0x0 roaming=NO rxBytes=14410 rxPackets=66 txBytes=10290 txPackets=85 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [15] iface=wlan0 uid=10063 set=FOREGROUND tag=0x0 roaming=NO rxBytes=2495802 rxPackets=2865 txBytes=650496 txPackets=2694 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [16] iface=wlan0 uid=10086 set=DEFAULT tag=0x0 roaming=NO rxBytes=5876 rxPackets=12 txBytes=2333 txPackets=11 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [17] iface=wlan0 uid=10086 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [18] iface=wlan0 uid=10088 set=DEFAULT tag=0x0 roaming=NO rxBytes=10832 rxPackets=32 txBytes=6307 txPackets=38 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [19] iface=wlan0 uid=10088 set=FOREGROUND tag=0x0 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [20] iface=wlan0 uid=10013 set=DEFAULT tag=0x600 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [21] iface=wlan0 uid=10013 set=FOREGROUND tag=0x600 roaming=NO rxBytes=5112 rxPackets=11 txBytes=2349 txPackets=11 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [22] iface=wlan0 uid=10036 set=DEFAULT tag=0x600 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [23] iface=wlan0 uid=10036 set=FOREGROUND tag=0x600 roaming=NO rxBytes=40758 rxPackets=38 txBytes=2572 txPackets=23 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [24] iface=wlan0 uid=10013 set=DEFAULT tag=0x10000407 roaming=NO rxBytes=1103 rxPackets=9 txBytes=939 txPackets=7 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [25] iface=wlan0 uid=10013 set=FOREGROUND tag=0x10000407 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [26] iface=wlan0 uid=10013 set=DEFAULT tag=0x10001301 roaming=NO rxBytes=9400 rxPackets=16 txBytes=2977 txPackets=17 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [27] iface=wlan0 uid=10013 set=FOREGROUND tag=0x10001301 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [28] iface=wlan0 uid=10013 set=DEFAULT tag=0x20000407 roaming=NO rxBytes=5829 rxPackets=14 txBytes=3943 txPackets=13 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [29] iface=wlan0 uid=10013 set=FOREGROUND tag=0x20000407 roaming=NO rxBytes=0 rxPackets=0 txBytes=0 txPackets=0 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [30] iface=wlan0 uid=10013 set=DEFAULT tag=0x21065fff roaming=NO rxBytes=8662 rxPackets=30 txBytes=24691 txPackets=31 operations=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): [31] iface=wlan0 uid=10013 set=FOREGROUND tag=0x21065fff roaming=NO rxBytes=0 rxPackets=0 txBytes=0
05-12 22:03:24.430 I/TetherStatsReporting( 2310): combining tether stats
05-12 22:03:24.432 D/QtiTetherService/IpaWrapper( 3175): getStats(false)
05-12 22:03:24.436 I/GnssLocationProvider( 2310): WakeLock acquired by sendMessage(5, 0, null)
05-12 22:03:24.436 I/GnssLocationProvider( 2310): WakeLock acquired by sendMessage(6, 0, null)
05-12 22:03:24.437 W/QCNEJ ( 3175): |CORE| network available: 107
05-12 22:03:24.440 W/QCNEJ ( 3175): |CORE| onAvailable: bind the process to WIFI
05-12 22:03:24.443 W/QCNEJ ( 3175): |CORE| newLp: {InterfaceName: wlan0 LinkAddresses: [fe80::ce9f:7aff:fe01:2b22/64,172.31.0.9/24,] Routes: [fe80::/64 -> :: wlan0,172.31.0.0/24 -> 0.0.0.0 wlan0,0.0.0.0/0 -> 172.31.0.1 wlan0,] DnsAddresses: [172.31.0.1,] Domains: null MTU: 0 TcpBufferSizes: 524288,1048576,2097152,262144,524288,1048576}
05-12 22:03:24.444 W/QCNEJ ( 3175): |CORE| curLp: {InterfaceName: wlan0 LinkAddresses: [fe80::ce9f:7aff:fe01:2b22/64,172.31.0.9/24,] Routes: [fe80::/64 -> :: wlan0,172.31.0.0/24 -> 0.0.0.0 wlan0,0.0.0.0/0 -> 172.31.0.1 wlan0,] DnsAddresses: [172.31.0.1,] Domains: null MTU: 0}
MikroTik hAP acで作るHotspot 2.0環境 (プロファイルをインストールできない端末のログを見てみる)
MikroTik hAP acで作るHotspot 2.0環境 (Android編) - pirosapの備忘録の続き。
前回作ったAndroid用のプロファイルは、Nexus 5XのAndroid 7.1.1/Android O developer previewではインストールできるものの、Android One 507SHにおいては6.0.1/7.0/7.1.1全てインストールできない。
何故?ということで、実機のログを見てみる。
実機を開発者向けオプションから、USBデバッグを有効にして、PCとUSBで接続する。
実機はAndroid 7.1.1にアップデート済のAndroid One 507SH。Android Oneはメーカ独自のカスタマイズが少ないと見込んで選んだ。
ちょいちょい関係ないログも混じっていると思われる。
$ adb logcat -v time
(略)
05-06 16:37:40.116 I/ActivityManager( 1253): START u0 {act=android.intent.action.VIEW dat=content://downloads/all_downloads/34 typ=application/x-wifi-config flg=0x10000001 cmp=com.android.certinstaller/.CertInstallerMain} from uid 10042 on display 0
05-06 16:37:40.164 I/ActivityManager( 1253): Start proc 7972:com.android.certinstaller/u0a41 for activity com.android.certinstaller/.CertInstallerMain
05-06 16:37:40.210 W/System ( 7972): ClassLoader referenced unknown path: /system/app/CertInstaller/lib/arm
05-06 16:37:40.282 I/ActivityManager( 1253): START u0 {cmp=com.android.certinstaller/.WiFiInstaller (has extras)} from uid 10041 on display 0
05-06 16:37:40.343 I/Adreno ( 7972): QUALCOMM build : 602b6aa, Ic1695e72bc
05-06 16:37:40.343 I/Adreno ( 7972): Build Date : 07/28/16
05-06 16:37:40.343 I/Adreno ( 7972): OpenGL ES Shader Compiler Version: XE031.09.00.03
05-06 16:37:40.343 I/Adreno ( 7972): Local Branch :
05-06 16:37:40.343 I/Adreno ( 7972): Remote Branch : refs/tags/AU_LINUX_ANDROID_LA.BR.1.3.6.06.00.01.005.033
05-06 16:37:40.343 I/Adreno ( 7972): Remote Branch : NONE
05-06 16:37:40.343 I/Adreno ( 7972): Reconstruct Branch : NOTHING
05-06 16:37:40.347 D/WifiInstaller( 7972): WiFi data for wifi-config: application/x-wifi-config is 7141
05-06 16:37:40.350 D/WCFG ( 1253): Content: 7141
05-06 16:37:40.350 D/WCFG ( 1253): Decoded: 5286 bytes.
05-06 16:37:40.352 D/HS20 ( 1253): plain MIME container, boundary '{boundary}', type 'application/x-passpoint-profile', encoding [base64]
05-06 16:37:40.353 D/HS20 ( 1253): plain MIME container, boundary '{boundary}', type 'application/x-x509-ca-cert', encoding [base64]
05-06 16:37:40.353 I/OpenGLRenderer( 7972): Initialized EGL, version 1.4
05-06 16:37:40.354 D/OpenGLRenderer( 7972): Swap behavior 1
05-06 16:37:40.354 D/HS20 ( 1253): multipart MIME container, boundary 'null', type 'multipart/mixed', encoding [base64]
05-06 16:37:40.354 D/WCFG ( 1253): + Content Type: application/x-passpoint-profile
05-06 16:37:40.354 D/WCFG ( 1253): OMA: <MgmtTree xmlns="syncml:dmddf1.2">
05-06 16:37:40.354 D/WCFG ( 1253): <VerDTD>1.2</VerDTD>
05-06 16:37:40.354 D/WCFG ( 1253): <Node>
05-06 16:37:40.354 D/WCFG ( 1253): <NodeName>PerProviderSubscription</NodeName>
05-06 16:37:40.354 D/WCFG ( 1253): <RTProperties>
05-06 16:37:40.354 D/WCFG ( 1253): <Type>
05-06 16:37:40.354 D/WCFG ( 1253): <DDFName>urn:wfa:mo:hotspot2dot0-perprovidersubscription:1.0</DDFName>
05-06 16:37:40.354 D/WCFG ( 1253): </Type>
05-06 16:37:40.354 D/WCFG ( 1253): </RTProperties>
05-06 16:37:40.354 D/WCFG ( 1253): <Node>
05-06 16:37:40.354 D/WCFG ( 1253): <NodeName>X1</NodeName>
05-06 16:37:40.354 D/WCFG ( 1253): <Node>
05-06 16:37:40.354 D/WCFG ( 1253): <NodeName>Credential</NodeName>
05-06 16:37:40.354 D/WCFG ( 1253): <Node>
05-06 16:37:40.354 D/WCFG ( 1253): <NodeName>CreationDate</NodeName>
05-06 16:37:40.354 D/WCFG ( 1253): <Value>2017-02-16T14:21:36Z</Value>
05-06 16:37:40.354 D/WCFG ( 1253): </Node>
05-06 16:37:40.354 D/WCFG ( 1253): <Node>
05-06 16:37:40.354 D/WCFG ( 1253): <NodeName>UsernamePassword</NodeName>
05-06 16:37:40.354 D/WCFG ( 1253): <Node>
05-06 16:37:40.354 D/WCFG ( 1253): <NodeName>MachineManaged</NodeName>
05-06 16:37:40.354 D/WCFG ( 1253): <Value>true</Value>
05-06 16:37:40.354 D/WCFG ( 1253): </Node>
05-06 16:37:40.354 D/WCFG ( 1253): <Node>
05-06 16:37:40.354 D/WCFG ( 1253): <NodeName>EAPMethod</NodeName>
05-06 16:37:40.354 D/WCFG ( 1253): <Node>
05-06 16:37:40.354 D/WCFG ( 1253): <NodeName>EAPType</NodeName>
05-06 16:37:40.354 D/WCFG ( 1253): <Value>21</Value>
05-06 16:37:40.354 D/WCFG ( 1253): </Node>
05-06 16:37:40.354 D/WCFG ( 1253): <Node>
05-06 16:37:40.354 D/WCFG ( 1253): <NodeName>InnerMethod</NodeName>
05-06 16:37:40.354 D/WCFG ( 1253): <Value>MS-CHAP-V2</Value>
05-06 16:37:40.354 D/WCFG ( 1253): </Node>
05-06 16:37:40.354 D/WCFG ( 1253): </Node>
05-06 16:37:40.354 D/WCFG ( 1253): <Node>
05-06 16:37:40.354 D/WCFG ( 1253): <NodeName>Username</NodeName>
05-06 16:37:40.354 D/WCFG ( 1253): <Value>hoge</Value>
05-06 16:37:40.354 D/WCFG ( 1253): </Node>
05-06 16:37:40.354 D/WCFG ( 1253): <Node>
05-06 16:37:40.354 D/WCFG ( 1253): <NodeName>Password</NodeName>
05-06 16:37:40.354 D/WCFG ( 1253): <Value>aHMyMCF0ZXN0MTc=</Value>
05-06 16:37:40.354 D/WCFG ( 1253): </Node>
05-06 16:37:40.354 D/WCFG ( 1253): </Node>
05-06 16:37:40.354 D/WCFG ( 1253): <Node>
05-06 16:37:40.354 D/WCFG ( 1253): <NodeName>Realm</NodeName>
05-06 16:37:40.354 D/WCFG ( 1253): <Value>pirosap.tech</Value>
05-06 16:37:40.354 D/WCFG ( 1253): </Node>
05-06 16:37:40.354 D/WCFG ( 1253): </Node>
05-06 16:37:40.354 D/WCFG ( 1253): <Node>
05-06 16:37:40.354 D/WCFG ( 1253): <NodeName>HomeSP</NodeName>
05-06 16:37:40.354 D/WCFG ( 1253): <Node>
05-06 16:37:40.354 D/WCFG ( 1253): <NodeName>FriendlyName</NodeName>
05-06 16:37:40.354 D/WCFG ( 1253): <Value>NGH testbed by pirosap.tech</Value>
05-06 16:37:40.354 D/WCFG ( 1253): </Node>
05-06 16:37:40.354 D/WCFG ( 1253): <Node>
05-06 16:37:40.354 D/WCFG ( 1253): <NodeName>FQDN</NodeName>
05-06 16:37:40.354 D/WCFG ( 1253): <Value>ngh.pirosap.tech</Value>
05-06 16:37:40.354 D/WCFG ( 1253): </Node>
05-06 16:37:40.354 D/WCFG ( 1253): </Node>
05-06 16:37:40.354 D/WCFG ( 1253): </Node>
05-06 16:37:40.354 D/WCFG ( 1253): </Node>
05-06 16:37:40.354 D/WCFG ( 1253): </MgmtTree>
05-06 16:37:40.355 D/WCFG ( 1253): + Content Type: application/x-x509-ca-cert
05-06 16:37:40.356 D/WCFG ( 1253): Cert subject CN=DST Root CA X3, O=Digital Signature Trust Co.
05-06 16:37:40.361 D/WCFG ( 1253): Full Cert: Certificate:
05-06 16:37:40.361 D/WCFG ( 1253): Data:
05-06 16:37:40.361 D/WCFG ( 1253): Version: 3 (0x2)
05-06 16:37:40.361 D/WCFG ( 1253): Serial Number:
05-06 16:37:40.361 D/WCFG ( 1253): 44:af:b0:80:d6:a3:27:ba:89:30:39:86:2e:f8:40:6b
05-06 16:37:40.361 D/WCFG ( 1253): Signature Algorithm: sha1WithRSAEncryption
05-06 16:37:40.361 D/WCFG ( 1253): Issuer: O=Digital Signature Trust Co., CN=DST Root CA X3
05-06 16:37:40.361 D/WCFG ( 1253): Validity
05-06 16:37:40.361 D/WCFG ( 1253): Not Before: Sep 30 21:12:19 2000 GMT
05-06 16:37:40.361 D/WCFG ( 1253): Not After : Sep 30 14:01:15 2021 GMT
05-06 16:37:40.361 D/WCFG ( 1253): Subject: O=Digital Signature Trust Co., CN=DST Root CA X3
05-06 16:37:40.361 D/WCFG ( 1253): Subject Public Key Info:
05-06 16:37:40.361 D/WCFG ( 1253): Public Key Algorithm: rsaEncryption
05-06 16:37:40.361 D/WCFG ( 1253): Public-Key: (2048 bit)
05-06 16:37:40.361 D/WCFG ( 1253): Modulus:
05-06 16:37:40.361 D/WCFG ( 1253): 00:df:af:e9:97:50:08:83:57:b4:cc:62:65:f6:90:
05-06 16:37:40.361 D/WCFG ( 1253): 82:ec:c7:d3:2c:6b:30:ca:5b:ec:d9:c3:7d:c7:40:
05-06 16:37:40.361 D/WCFG ( 1253): c1:18:14:8b:e0:e8:33:76:49:2a:e3:3f:21:49:93:
05-06 16:37:40.361 D/WCFG ( 1253): ac:4e:0e:af:3e:48:cb:65:ee:fc:d3:21:0f:65:d2:
05-06 16:37:40.361 D/WCFG ( 1253): 2a:d9:32:8f:8c:e5:f7:77:b0:12:7b:b5:95:c0:89:
05-06 16:37:40.361 D/WCFG ( 1253): a3:a9:ba:ed:73:2e:7a:0c:06:32:83:a2:7e:8a:14:
05-06 16:37:40.361 D/WCFG ( 1253): 30:cd:11:a0:e1:2a:38:b9:79:0a:31:fd:50:bd:80:
05-06 16:37:40.361 D/WCFG ( 1253): 65:df:b7:51:63:83:c8:e2:88:61:ea:4b:61:81:ec:
05-06 16:37:40.361 D/WCFG ( 1253): 52:6b:b9:a2:e2:4b:1a:28:9f:48:a3:9e:0c:da:09:
05-06 16:37:40.361 D/WCFG ( 1253): 8e:3e:17:2e:1e:dd:20:df:5b:c6:2a:8a:ab:2e:bd:
05-06 16:37:40.361 D/WCFG ( 1253): 70:ad:c5:0b:1a:25:90:74:72:c5:7b:6a:ab:34:d6:
05-06 16:37:40.361 D/WCFG ( 1253): 30:89:ff:e5:68:13:7b:54:0b:c8:d6:ae:ec:5a:9c:
05-06 16:37:40.361 D/WCFG ( 1253): 92:1e:3d:64:b3:8c:c6:df:bf:c9:41:70:ec:16:72:
05-06 16:37:40.361 D/WCFG ( 1253): d5:26:ec:38:55:39:43:d0:fc:fd:18:5c:40:f1:97:
05-06 16:37:40.361 D/WCFG ( 1253): eb:d5:9a:9b:8d:1d:ba:da:25:b9:c6:d8:df:c1:15:
05-06 16:37:40.361 D/WCFG ( 1253): 02:3a:ab:da:6e:f1:3e:2e:f5:5c:08:9c:3c:d6:83:
05-06 16:37:40.361 D/WCFG ( 1253): 69:e4:10:9b:19:2a:b6:29:57:e3:e5:3d:9b:9f:f0:
05-06 16:37:40.361 D/WCFG ( 1253): 02:5d
05-06 16:37:40.361 D/WCFG ( 1253): Exponent: 65537 (0x10001)
05-06 16:37:40.361 D/WCFG ( 1253): X509v3 extensions:
05-06 16:37:40.361 D/WCFG ( 1253): X509v3 Basic Constraints: critical
05-06 16:37:40.361 D/WCFG ( 1253): CA:TRUE
05-06 16:37:40.361 D/WCFG ( 1253): X509v3 Key Usage: critical
05-06 16:37:40.361 D/WCFG ( 1253): Certificate Sign, CRL Sign
05-06 16:37:40.361 D/WCFG ( 1253): X509v3 Subject Key Identifier:
05-06 16:37:40.361 D/WCFG ( 1253): C4:A7:B1:A4:7B:2C:71:FA:DB:E1:4B:90:75:FF:C4:15:60:85:89:10
05-06 16:37:40.361 D/WCFG ( 1253): Signature Algorithm: sha1WithRSAEncryption
05-06 16:37:40.361 D/WCFG ( 1253): a3:1a:2c:9b:17:00:5c:a9:1e:ee:28:66:37:3a:bf:83:c7:3f:
05-06 16:37:40.361 D/WCFG ( 1253): 4b:c3:09:a0:95:20:5d:e3:d9:59:44:d2:3e:0d:3e:bd:8a:4b:
05-06 16:37:40.361 D/WCFG ( 1253): a0:74:1f:ce:10:82:9c:74:1a:1d:7e:98:1a:dd:cb:13:4b:b3:
05-06 16:37:40.361 D/WCFG ( 1253): 20:44:e4:91:e9:cc:fc:7d:a5:db:6a:e5:fe:e6:fd:e0:4e:dd:
05-06 16:37:40.361 D/WCFG ( 1253): b7:00:3a:b5:70:49:af:f2:e5:eb:02:f1:d1:02:8b:19:cb:94:
05-06 16:37:40.361 D/WCFG ( 1253): 3a:5e:48:c4:18:1e:58:19:5f:1e:02:5a:f0:0c:f1:b1:ad:a9:
05-06 16:37:40.361 D/WCFG ( 1253): dc:59:86:8b:6e:e9:91:f5:86:ca:fa:b9:66:33:aa:59:5b:ce:
05-06 16:37:40.361 D/WCFG ( 1253): e2:a7:16:73:47:cb:2b:cc:99:b0:37:48:cf:e3:56:4b:f5:cf:
05-06 16:37:40.361 D/WCFG ( 1253): 0f:0c:72:32:87:c6:f0:44:bb:53:72:6d:43:f5:26:48:9a:52:
05-06 16:37:40.361 D/WCFG ( 1253): 67:b7:58:ab:fe:67:76:71:78:db:0d:a2:56:14:13:39:24:31:
05-06 16:37:40.361 D/WCFG ( 1253): 85:a2:a8:02:5a:30:47:e1:dd:50:07:bc:02:09:90:00:eb:64:
05-06 16:37:40.361 D/WCFG ( 1253): 63:60:9b:16:bc:88:c9:12:e6:d2:7d:91:8b:f9:3d:32:8d:65:
05-06 16:37:40.361 D/WCFG ( 1253): b4:e9:7c:b1:57:76:ea:c5:b6:28:39:bf:15:65:1c:c8:f6:77:
05-06 16:37:40.361 D/WCFG ( 1253): 96:6a:0a:8d:77:0b:d8:91:0b:04:8e:07:db:29:b6:0a:ee:9d:
05-06 16:37:40.361 D/WCFG ( 1253): 82:35:35:10ここらへんまでは良さげ。ちゃんとプロファイルの内容を読み取っている。
05-06 16:37:40.416 V/DownloadManager( 6879): Deleting /storage/emulated/0/Download/pirosap-tech-20170429.config via provider delete
05-06 16:37:40.419 D/MediaProvider( 6879): object removed 78
05-06 16:37:40.637 I/ActivityManager( 1253): Displayed com.android.certinstaller/.WiFiInstaller: +326ms (total +495ms)
05-06 16:37:40.787 W/WindowManager( 1253): Attempted to remove non-existing token: android.os.Binder@758837a
05-06 16:37:47.979 W/QCNEJ ( 4290): |CORE| CNE received unexpected action: android.intent.action.BATTERY_CHANGED
05-06 16:37:47.980 I/DownloadManagerWrapper( 6905): onReceive() : Charging = true
05-06 16:37:50.495 I/ActivityManager( 1253): Start proc 7994:com.google.android.apps.photos:CameraShortcut/u0a70 for service com.google.android.apps.photos/.camerashortcut.CameraShortcutServiceImpl
05-06 16:37:50.537 I/art ( 7994): Starting a blocking GC AddRemoveAppImageSpace
05-06 16:37:50.539 W/System ( 7994): ClassLoader referenced unknown path: /system/app/Photos/lib/arm
05-06 16:37:50.883 I/art ( 7994): Do partial code cache collection, code=0B, data=12KB
05-06 16:37:50.884 I/art ( 7994): After code cache collection, code=0B, data=12KB
05-06 16:37:50.884 I/art ( 7994): Increasing code cache capacity to 128KB
05-06 16:37:51.246 D/CryptdConnector( 1253): SND -> {17 cryptfs getpwtype}
05-06 16:37:51.246 D/VoldCryptCmdListener( 346): cryptfs getpwtype
05-06 16:37:51.252 D/CryptdConnector( 1253): RCV <- {213 17 default}
05-06 16:37:51.888 I/Babel_ConcService( 6673): Acquired partial wake lock to keep ConcurrentService alive
05-06 16:37:51.891 I/Babel_ConcService( 6673): Released partial wake lock as ConcurrentService became idle
05-06 16:37:53.690 I/MSM-irqbalance( 620): Decided to move IRQ166 from CPU7 to CPU6
05-06 16:37:54.513 I/Icing ( 4606): Usage reports 0 indexed 0 rejected 0 imm upload false
05-06 16:37:54.522 W/IcingInternalCorpora( 4606): getNumBytesRead when not calculated.
05-06 16:37:55.431 I/QtiTetherService( 4290): limitReached Alert received limitName: globalAlert on Interface: lo
05-06 16:37:55.532 I/Icing ( 4606): Indexing DCAFEA8F428F46304CB1907AEB6237632734F373 from com.android.chrome
05-06 16:37:55.659 I/Icing ( 4606): Indexing done DCAFEA8F428F46304CB1907AEB6237632734F373
05-06 16:37:56.163 I/addOrUpdateNetwork( 1253): uid = 10041 SSID null nid=-1
05-06 16:37:56.164 E/WifiConfigManager( 1253): Passpoint is not enabled
05-06 16:37:56.167 I/ActivityManager( 1253): START u0 {cmp=com.android.certinstaller/.CredentialsInstallDialog (has extras)} from uid 10041 on display 0
05-06 16:37:56.406 I/ActivityManager( 1253): Displayed com.android.certinstaller/.CredentialsInstallDialog: +212ms
05-06 16:37:56.635 W/Icing ( 4252): isOptedInForAppHistory: empty Account Name encountered
05-06 16:37:56.679 I/Icing ( 4606): Usage reports 1 indexed 0 rejected 0 imm upload false
05-06 16:37:57.706 I/Icing ( 4606): Usage reports 0 indexed 0 rejected 0 imm upload false
05-06 16:37:58.690 I/MSM-irqbalance( 620): Decided to move IRQ240 from CPU7 to CPU6
05-06 16:37:58.754 W/WindowManager( 1253): Attempted to remove non-existing token: android.os.Binder@74b7443うーん。
Passpoint is not enabled が気になるなあ。
Passpointが有効でないから、CredentialInstallDialogでインストール失敗を出しているように見える。
でも507SHにはWi-Fiの詳細設定とかにはPasspointを有効にするみたいなのはないんだよなあ。
うーん。
MikroTik RouterOSで利用可能な技適があるUSB接続の3G/LTEモデムを探してみた
RouterOSで認識して利用できる技適があるUSB接続の3G/LTEモデムまとめ。
公式のSupported Hardwareはこちら。Supported Hardware
日本の技適を取得しているデバイスは掲載されていないので、独自に検証してみた。
参考 3G/4G Solutions with RouterOS
RouterOSは、6.40rc2(MMIPS)。ハードウェアはhEX(RB750Gr3)にて検証。
基本的にはhAP acなどのMIPSBEでも同じ。
検証結果一覧
| Model | 備考 | 検証結果 | 検証日 |
|---|---|---|---|
| AndroidのUSBテザリング | SO-01Gで検証 | ○ 但しテザリングのためNATされる | - |
| L-03D(NTT Docomo) | LG | × /port usbで認識せず | 2017/05/04 |
| L-03F(NTT Docomo) | LG ※事前にPCでデータ通信専用モードに設定 | × NDIS、PPP共に/port usbで認識せず | 2017/05/04 |
| WM320(SIMフリー) | 富士ソフト | × /port usbで認識せず | 2017/05/04 |
| HX006ZT(Willcom) | ZTE MF633として認識 HX006ZT - ZTE Japan | ○ Docomo SIMで3G接続確認。moperaであればppp-outにグローバルIPアドレスが割り当てられる | 2017/05/04 |
| HX008ZT(Willcom) | Softbank 004Zとほぼ同じ? | 検証予定 | - |
| Doccica BM-DC1-500M(b-mobile) | ZTE MF636として認識 Doccica(ドッチーカ)詳細仕様 | b-mobile Doccica ※標準SIMじゃないと挿しにくい | ○ Docomo SIMで3G接続確認。moperaであればppp-outにグローバルIPアドレスが割り当てられる | 2017/05/04 |
| GL06P(EMOBILE) | HUAWEI | 検証予定 | - |
※L-03Fは白ロムとして入手しやすいので、MikroTikサポートにsupout.rifと共に対応可能かどうか依頼中。"We will see what can be done to add support."とのこと。
利用可デバイスの詳細
■HX006ZT (ZTE MF633)
[admin@MikroTik] > /system resource usb print detail
(略)
2 device="1:11" vendor="ZTE,Incorporated" name="ZTE WCDMA Technologies MSM"
serial-number="P673C1WILD010000" vendor-id="0x19d2" device-id="0x0016"
speed="480 Mbps" ports=0 usb-version="2.00"
[admin@MikroTik] > /port print detail
Flags: I - inactive
0 name="usb1" used-by="PPP <ppp-out1>" device="1:11" channels=3
baud-rate=9600 data-bits=8 parity=none stop-bits=1 flow-control=none
[admin@MikroTik] > system serial-terminal usb1 channel=2
[Ctrl-A is the prefix key]
at
OK
at+cgdcont?
+CGDCONT: 1,"IP","mopera.net","0.0.0.0",0,0
ignore-directip-modem は no
■Doccica BM-DC1-500M (ZTE MFM636)
SIMスロットはUSBコネクタの上。

標準SIMじゃないと挿しにくい。SIMカードアダプタ危険かも(抜けなくなりそう)。
[admin@MikroTik] > /system resource usb print detail (略) 2 device="1:19" vendor="ZTE,Incorporated" name="ZTE CDMA Technologies MSM" serial-number="1234567890ABCDEF" vendor-id="0x19d2" device-id="0x0031" speed="480 Mbps" ports=0 usb-version="2.00" [admin@MikroTik] > /system serial-terminal usb2 channel=2 [Ctrl-A is the prefix key] ati Manufacturer: ZTE INCORPORATED Model: MF636 Revision: BD_JCIP673M2V1.0.0B01 IMEI: 352847026918811 +GCAP: +CGSM,+DS,+ES OK at+cgdcont? +CGDCONT: 1,"IP","open.mopera.net","0.0.0.0",0,0
src-nat、Firewallなどの設定は環境に合わせて適時設定。